Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
December 2021
AWS Pentest Beginners Guide - Tools and Techniques
What is Digital Risk? Learn how to Manage it
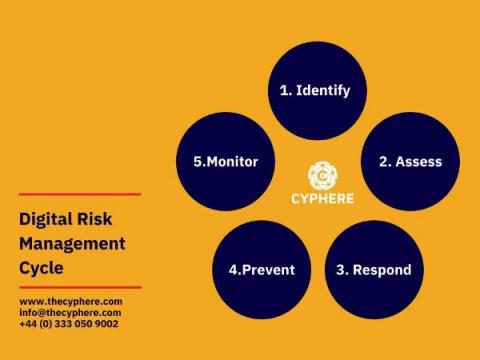
Digital risks are a big issue for today’s society. Digital risks can be anything from stealing sensitive information to exposing your own personal information to the public. This is why an understanding of the digital risk management process helps businesses to identify and protect themselves.
What are Traffic Bots? Methods to detect and stop Bot traffic!
Bot traffic is a type of traffic that is generated by automated programs, or bots. These bots can be used to generate fake traffic for testing purposes or to engage in malicious activities. Malicious bot traffic is a huge problem for many website owners, and bot detection can be difficult. There are various types of bot traffic that you need to watch out for. In this guide, we will discuss their different types and how to combat them!
What is Domain Hijacking? Tips to Protect yourself
Domain hijacking is the act of domain name theft. It can happen to individuals or organisations and it’s increasing in frequency. The name may be hijacked by someone else who passes themselves off as you, tricks your domain registrar into transferring your domain to them, or hacks into your account (sometimes through phishing) and transfers it themselves.
LDAP Server Guide - How Does It Work?
Sensitive Data: What is it, and why you should never share it.
Cybersecurity Architecture: A Complete Guide to Preparing Your Organization for a Cyberattack
VoIP Security. How secure is your VoIP?
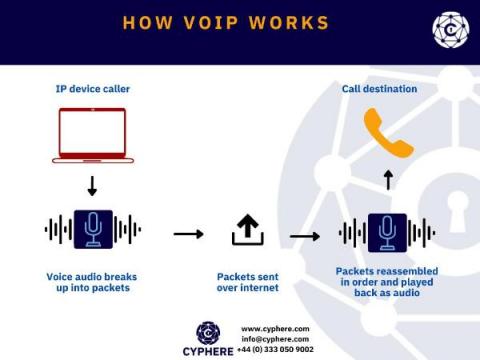
For over a century we have seen voice communication being made over Public Switched Telephone Network (PSTN), but since the past decade or two Voice over IP (VoIP) has been introduced and quickly adopted throughout the world for making business phone calls.
Top Cybersecurity Metrics (KPI) to Track
Cyber security KPI or other Key Performance Indicators are established in different areas of every organisation to track and monitor the progress towards attaining a certain goal or target. Cybersecurity is no exception here, and companies should maintain proper cybersecurity KPIs. There are many blog posts available around this topic but in this article, we have gathered a list of important cybersecurity KPIs that every organisation should consider.
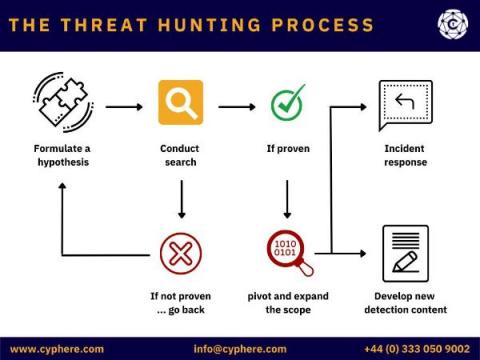
Threat hunting: Process, Methodologies, Tools and Tips
In cyber security, threat hunting is the act of proactively searching and monitoring networks, systems, endpoints, datasets etc. to identify any malicious behaviours or patterns that are not detected by existing security tools.
PHP Security 101 + 1
PHP is by far the most widely used server-side programming language. Security threats surrounding PHP applications have been in the news because PHP captures over 80% of the internet with over 10 million websites built. It’s no wonder that with such a massive usage, PHP is also one of the most targeted and exploited languages, as shown in the below statistics.
Information Security Controls | Different Types and Purpose Explained
Security risks of Cloud Computing | Threats, Issues and Challenges
CVE-2021-44228 - Log4j zero day vulnerability, detection and Log4shell fix
Log4j zero-day vulnerability is flooding the security updates/news everywhere. This issue has been named Log4shell and assigned CVE-2021-44228 (still awaiting analysis at the time of writing).
Jailbreaking an iPhone: Should you Jailbreak yours?
The technical term jailbreaking implies that a locked-down electronic device has been changed to remove restrictions and allow the installation of unauthorised software. Although the term contains breaking, it doesn’t involve breaking anything physically.
What is Security as a Service? Advantages and Use of SECaas
Cyber security is a serious concern for businesses in the digital age. It is not uncommon these days to see businesses spending big amounts on security solutions that are difficult to maintain and even more expensive to upgrade. For this reason, security as a service (SECaaS) has gained traction because it allows businesses to outsource their security needs reliably without having to go through the hassle of investing in resources and solutions.
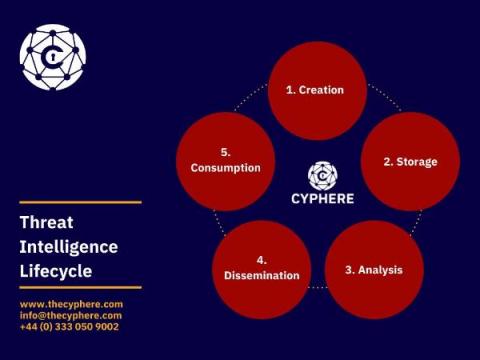
Threat Intelligence: Everything You Need to Know
This blog post will discuss the definition of threat intelligence and different stages of the threat intelligence cycle to help you better understand what happens behind the scenes.
What are Zero day Attacks? - A Comprehensive Guide
Cyber threats and attacks are a growing issue for businesses because the amount of vulnerabilities has increased. The volume of global malware has risen 58% annually, and the volume of spam has risen by more than one-third in the past 12 months. These issues have made it more difficult for employees to focus on what they need to do. Zero-day attacks in cyber security are one such challenge for security teams around the world.