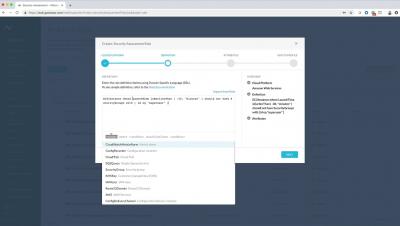
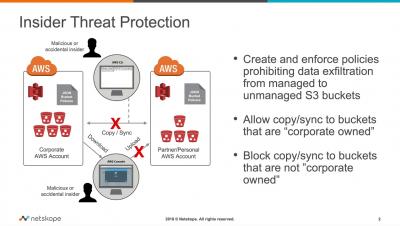
5 Reasons Why Your Business Needs Penetration Testing
Nowadays, high-profile security breaches continue to dominate the media headlines. This trend places an increasing number of businesses at risk. They are growing in amount and complexity while malicious hackers are actively developing new and more sophisticated forms of attacks every single day.