Challenges with Cybersecurity Asset Identification and Management
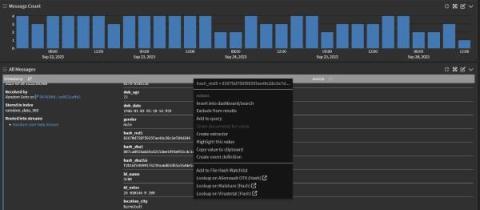
Anyone who’s ever misplaced their wallet knows that horrible moment where their stomach drops, the beads of perspiration begin to form on their forehead, and they start mulling over worst-case scenarios. In that worst case scenario, someone used the cash and cards in the wallet to go on a personal spending spree. In a company’s IT environment, a missing device or shadow IT represents that missing wallet.