Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
UTMStack
Automated Vulnerability Scan To Protect Your Business
A vulnerability scan is an automated process that identifies vulnerabilities (security holes) in any software, operating system, or network that bad actors can exploit. In essence, it’s an integral component of vulnerability management focused on protecting businesses from breaches and the exposure of sensitive data.
Multi-tenant Cloud Architecture
Today organizations have been able to recognize over the years the benefits of implementing a Cloud-based SIEM Service in terms of scalability, cost, and security. However, before operating in the cloud, you should know what architecture you need to adopt to protect your business and your customers’ data. Intending to help you implement a cost-effective SaaS SIEM Service, we share the advantages of multi-tenant over a single-tenant cloud architecture.
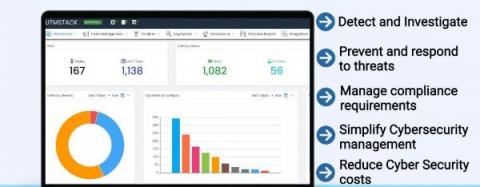
An Overview of UTMStack Features.
Best Dark Web Monitoring Tools
The dark web is a part of the internet that is not indexed by search engines and is only accessible through specific browsers. It has become a haven for all sorts of illegal activities and people who want to remain anonymous, including hackers. Often, the hackers use the dark web to sell steal passwords, compromising the security of employees and companies.
SIEM as a Service
SIEM-as-a-Service (SaaS) and Managed SIEM services have gained popularity among companies aiming to meet security compliance standards in a cost-effective manner. Let’s see why a SIEM service can transform your small or mid-sized business’s cybersecurity.
Cost-effective Managed SIEM Service
Contract with a third-party for managed SIEM services is increasingly affordable and requested by all-size organizations. Without any doubt, the advantages associated with this service allow monitoring, analyzing, and responding to cyber security threats more cost-effectively. However, what is a managed SIEM precisely? Is the price the only feature to take into account? What is the difference between a managed SIEM Provider (MSP) and a Managed Security Service Provider (MSSP)?
Using event correlation and AI for Threat Detection and Incident Response
According to Cybersecurity Ventures, cybercrime will cost the world $10.5 trillion annually by 2025. However, it is alarming how many companies are unaware of the aftermath of being attacked. A successful attack can cause irreversible damage to companies’ finances. This is because attacks include money theft, damage, and destruction of data, interruption in services, decreased productivity, theft of intellectual property, theft of personal and financial data, reputational harm, and others.