Impersonation attacks leverage Silicon Valley Bank collapse in new phishing campaign
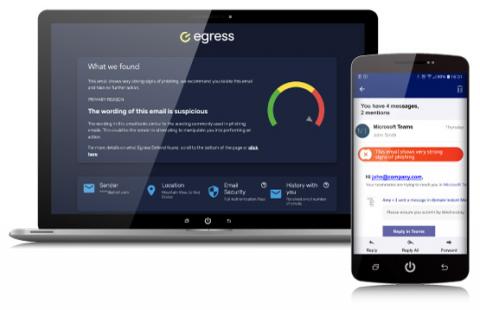
As news of Silicon Valley Bank’s (SVB) collapse continues to dominate the headlines, cybercriminals are running phishing campaigns impersonating SVB and other financial institutions, including M-F-A and Bloomberg. Responding quickly to the 24-hour news cycle, cybercriminals aim to leverage their victims’ potential distress over their financial situation to make them more susceptible to this type of attack.