Crystal Rans0m: Emerging hybrid ransomware with stealer capabilities
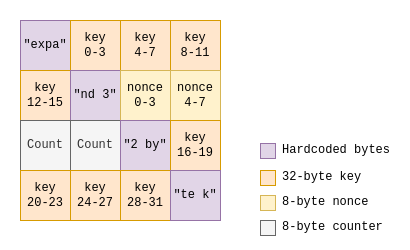
Crystal Rans0m is a previously undocumented hybrid ransomware family developed in Rust programming language seen for the first time in the wild on September 2nd, 2023. Interestingly, it does not only encrypt victim’s files, demanding a ransom for their release, but also steals sensitive information from the infected systems. This dual-threat approach means that attackers can double their leverage over victims, potentially increasing their chances of monetizing their attacks.