Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
CrowdStrike
Simple. Fast. Easy. How Deployments Should be.
Relentless Threat Activity Puts Identities in the Crosshairs
One set of valid employee credentials can provide an adversary with all they need to log into a business, move laterally, escalate privileges and achieve their goals — whether that’s removing access to accounts, terminating services, destroying data or deleting resources. Identity-based attacks are subtle, but destructive, and organizations must be on high alert for them. CrowdStrike reported 80% of cyberattacks now leverage stolen or compromised credentials.
Accelerate Your Security Transformation with Google Workspace and CrowdStrike
Each day, enterprise and public sector IT teams face new challenges when managing hybrid work for networks of hundreds, or even thousands, of users. A more distributed workforce means an increased reliance on collaboration and productivity tools. It also requires a strong strategy to protect these systems against vulnerabilities and modern cyberattacks.
Introducing CrowdStream: Simplifying XDR Adoption and Solving Security's Data Challenge
Stronger together. Never has an RSA conference theme been more aligned to CrowdStrike’s mission and vision for the future. If you look at our presence at RSAC 2023, CrowdStrike sits at the center of the security ecosystem. Everything we’re doing — from our partner breakfast to partner talks in our booth to our company announcements — highlights our commitment to bringing together the world’s best technology and data to deliver the best security outcomes.
MXDR Demo: Eradicating Multi-Vector Fileless Malware Attack in Minutes
Under the Wing: Protecting Small Businesses Against Big Attacks
Introducing CrowdStrike Falcon Complete XDR: Solving the Cybersecurity Skills Gap with Managed XDR
CrowdStrike today introduced CrowdStrike Falcon® Complete XDR, a new managed extended detection and response (MXDR) service that builds on the industry-leading CrowdStrike Falcon® Complete managed detection and response (MDR) service to give customers 24/7 expert-driven management, threat hunting, monitoring and end-to-end remediation across all key attack surfaces to close the cybersecurity skills gap.
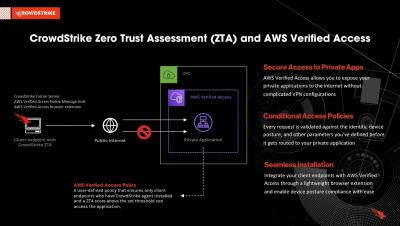
Securing private applications with CrowdStrike Zero Trust Assessment and AWS Verified Access
CrowdStrike Delivers Cyber Resilience for the Airline Industry to Meet New TSA Requirements
The U.S. Transportation Security Administration (TSA) is taking proactive measures to protect the nation’s transportation system by issuing new cybersecurity requirements for airports and aircraft operators. These emergency actions from TSA are part of the plan to increase the cyber resiliency of critical infrastructure and prevent their degradation or disruption.