Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Sysdig
Ten considerations for securing cloud and containers
Most organizations adopt cloud and containers to accelerate application development, but by adopting a secure DevOps approach and embedding security into the DevOps workflow, you can ensure security controls don’t slow down developers. Check out these key considerations to keep in mind as you put together your plan for securing clouds and containers.
Hunting AWS RDS Security Events with Sysdig
The AWS RDS service itself falls on the AWS side of the Shared Responsibility model, but the day-to-day management of the RDS security instances falls on your side. When it comes to shared responsibility, your obligation depends on the AWS services that you deploy, and also other factors including (but not limited to) the sensitivity of your data, your company’s requirements, and applicable laws and regulations.
Beekeeper Serves Up Secure Communications, Data, and Applications Across Cloud Environments with Sysdig
Beekeeper is known as one of the world’s top platforms for helping remote employees stay connected with their customers, other front-line workers, and the data they need to be successful. Through the company’s platform, employees can gain access to training, forms, and other work-based resources that require flawless access every time.
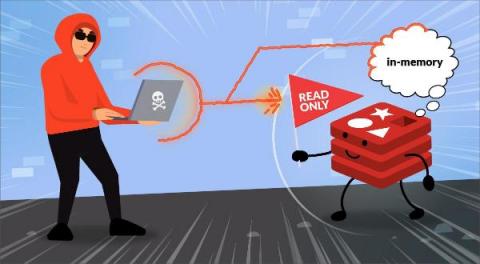
Compromising Read-Only Containers with Fileless Malware
Containers provide a number of security features that are not simply available on a normal host. One of those is the ability to make the container’s root filesystem read-only. By making the file system unable to be altered, it prevents an attacker from writing their malware executable to disk. Most attacks rely on writing files in order to work, but sophisticated cases use fileless malware as part of their malicious behavior.
What's new in Sysdig - April 2022
Welcome to another iteration of What’s New in Sysdig in 2022! Before starting, once again Happy Easter, Happy Passover, Happy Rama Navami, and Ramadan Mubarak! In general, happy spring break, and we hope you recovered from the chocolate egg drop.
Preventing cloud and container vulnerabilities
Vulnerabilities are software bugs or weaknesses that could be used by an attacker. They could be present in the operating system, application code, and third-party code dependencies, such as libraries, frameworks, programming scripts, and so on. By taking a secure DevOps approach and identifying vulnerabilities early in development, you avoid frustrating developers with delays when an application is ready for production.
Reducing vulnerability noise with Sysdig
Are vulnerability scores misleading you? Understanding CVSS severity and using them effectively
Vulnerabilities are everywhere. Vetting, mitigating, and remediating them at scale is exhausting for security practitioners. Let’s keep in mind that no organization has the capacity to find and fix all vulnerabilities. The key is to understand what a vulnerability is, interpret the meanings of the CVSS score, and prioritize and effectively use resources within constrained time limits or delivery windows. Since 2016, new vulnerabilities reported each year have nearly tripled.
Eliminate noise and prioritize the vulnerabilities that really matter with Risk Spotlight
Is your team drowning in container vulnerability noise? Are you spending a lot of time figuring out where to focus resources on and still missing dangerous vulnerabilities? Know that you are not alone. Container environments revolutionized app development by enabling unprecedented velocity, but not without a price. The use of readily available container images of third-party and open-source code enabled much faster cycles, but also facilitated the introduction of vulnerabilities in the application.