Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
SAP
In this video, we will show you Lookout CASB can help your IT security team prevent sensitive data from being exfiltrated from SAP SuccessFactors. We do this by detecting sensitive data using data loss prevention (DLP) and encrypting data upon download with Enterprise Digital Rights Management (EDRM). This ensure your data remains both inside and outside your organization.
Preventing Insider Threats in SAP SuccessFactors
In this video, we will show you how Lookout CASB provides you visibility into insider threats and privileged user activities. By using deep application awareness and intelligence, Lookout can detect various activities such as edits, exports, and other activities. We then surface this information in user-friendly and intuitive dashboards.
Protect SAP HANA on IBM Power Systems with Rubrik Zero Trust Data Security
SAP HANA is often a database of choice for large enterprises looking to drive more significant insights and quick decision-making through real-time or advanced analytics. As a result, SAP HANA has become key to driving day-to-day operations for many organizations and must be protected to guarantee maximum availability. However, managing this protection is no easy feat.
How SECUDE HALOCORE helps Infosys extend data protection outside the organization
Infosys is a global leader in next-generation digital services and consulting. It enables clients in 46 countries to navigate their digital transformation. With $13 Billion USD as its last 12 month’s revenue, serving a client base of 1500 customers, human capital of 249K employees, and managing millions of square feet of real estate.
Securing SAP SuccessFactors to remain compliant
Lookout is the only CASB in the SAP Store, and the only CASB vendor in the SAP integration partner lineup. We’ve worked closely with SAP to understand how SuccessFactors interacts with users and handles data. Recognized by Gartner as an industry-leading solution, Lookout CASB has built-in advanced data security and user and entity behavior analytics. But we wanted to ensure we can safeguard SuccessFactors and its vast functionalities, that’s why we worked hard to understand how the HCM solution interacts with users and handles data.
SECUDE and Turnkey Announce Strategic Technology Partnership
LUCERNE, NOVEMBER 2021: SECUDE, an established global security solutions provider offering innovative data protection for users of SAP and CAD/PLM software is pleased to announce the recently formed competency partnership with Turnkey Consulting Ltd., the world’s Risk, Identity, and Security specialists.
October 2021 Roundup - Latest News, Trends & Updates in Data Centric Security
Nearly all U.S. executives (98%) report that their organizations experienced at least one cyber event in the past year, compared to a slightly lower rate of 84% in non-U.S. executives, according to Deloitte’s 2021 Future of Cyber Survey. Further, COVID-19 pandemic disruption led to increased cyber threats to U.S. executives’ organizations (86%) at a considerably higher rate than non-U.S. executives experienced (63%). Yet, 14% of U.S.
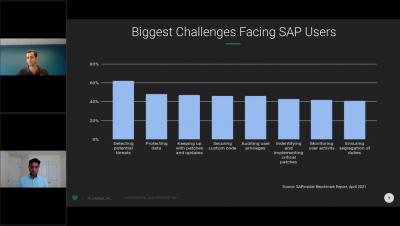
How to Detect SAP Threats in Real-Time with LogSentinel SIEM?
When it comes to the security of SAP systems, SIEM products often fail to meet companies’ expectations as they couldn’t fully interpret the SAP logs. LogSentinel Next-Gen SIEM solves this problem, eliminating the blind spots, as well as all SAP threats, and successfully parsing every log file in a human-readable format.
How to Detect SAP Threats in Real-Time with LogSentinel SIEM?
Find Out How to Easily Set Up Logsentinel Siem in Just a Few Step and Be Able to Detect and Respond to Any Sap Security Threats.
How SECUDE's HALOCORE complements Microsoft 365 E5 Compliance for securing sensitive SAP data
The new normal of working remotely calls for solutions that are seamless, flexible, and secure. Most enterprises believe that they are well-equipped to address the evolving cybersecurity threats. However, when employees connect through a myriad of devices, most of the time the security is highly questionable. This is because either they do not use secure devices or lack critical security updates. With cyberattacks becoming highly sophisticated, a host of security challenges awaits for the enterprise!