How to Secure AWS Route 53 with Sysdig
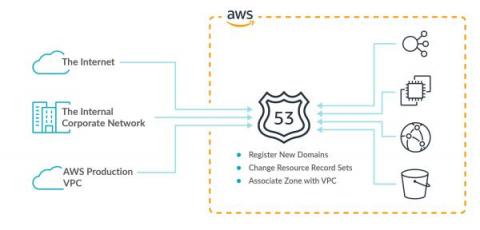
Either through human error or intentionally, configuration changes in the cloud may suddenly increase your attack surface. AWS Route 53 is an example of a service that needs to be continuously tracked for risky changes. As the first line of defense of our cloud, it is necessary to secure Amazon Route 53 and monitor risky configuration changes to avoid unwanted surprises. As you probably know, AWS Route 53 is of course a very popular DNS service offered by AWS, with millions of top-level domains.