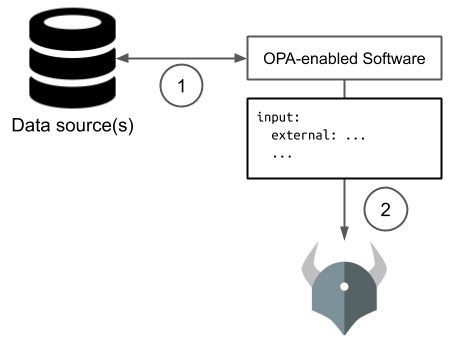
Fileless Malware Detection with Sysdig Secure
In today’s digital landscape, cyber threats continue to evolve at an alarming pace, with hackers constantly finding new ways to infiltrate systems and compromise sensitive data. One such sophisticated threat is fileless malware, a stealthy form of malicious software that operates entirely in the computer’s memory without leaving any trace on the hard drive.