Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Mobile
Where does mobile fit into security frameworks
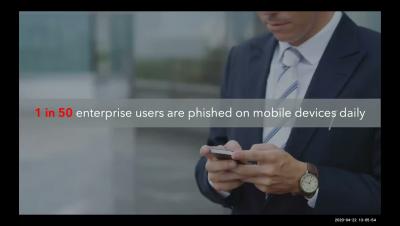
Phishing Threats in Mobile-enabled world
Steps to Stay Ahead of Risks and Protect Data Privacy
Technology has advanced our world in countless ways. Every day we bank, shop, conduct business and exchange photos and messages with family and friends online. While digital devices and services offer great convenience, they also pose risks to our data and privacy as the separation between our offline and online lives converges. Data Privacy Week, spanning January 24-28, serves as an important reminder of the importance of protecting our privacy and safeguarding personal information.
Under the Sheets, Practical Android Static Analysis
First off, before we get into the technical details of attacking applications, a few housekeeping bits must be understood. This blog is aimed at technical individuals that already understand at a basic level Android development and architecture, aiming to give security testers and application developers an insight into the ways an attacker may interrogate code to achieve some form of compromise.
Modernizing Government Cybersecurity with Zero Trust
Lookout CASB Use Case Demonstration
Get to Know Lookout
How a Large Financial Services Firm Protects Against Data Leakage with Lookout Secure Email Gateway
Regardless of the industry or organization, corporate email is the main cause of unauthorized and accidental data leaks. Employees are constantly sending emails to external parties that may contain sensitive company data, personally identifiable information (PII), trade secrets and other intellectual property.