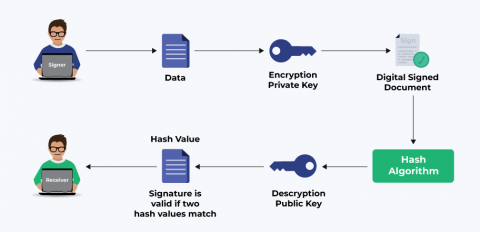
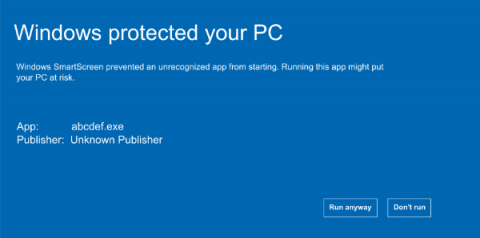
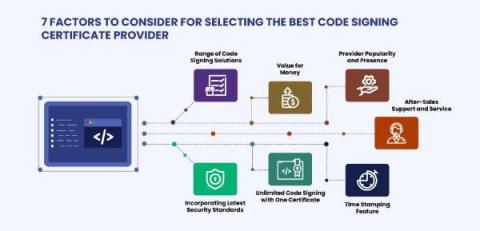
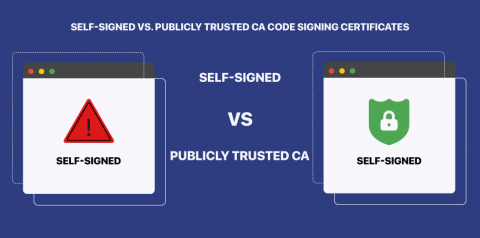
What are the Differences Between Encryption and Signing? Why Should You Use Digital Signatures?
While we have all used digital security certificates like SSL/TLS, code signing certificates, or others, many don’t know the security technology behind them. Stringent security standards ensure that the cyber threats looming around us never get to our digital systems. Due to such threats, there’s a constant advancement happening in data security technology to protect sensitive information. Encryption and Signing are two methods used widely for data security.