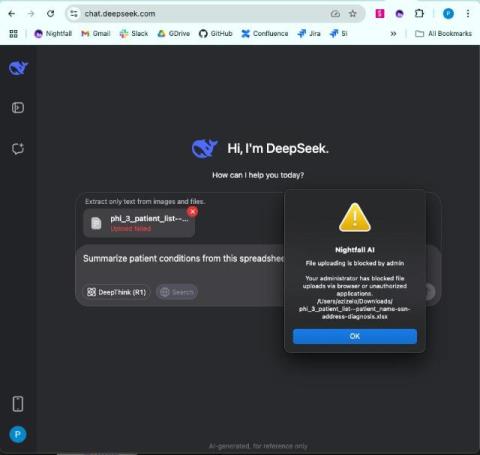
One-Stop Shop
All of your data security needs, in one place. Wasn’t that easy? Rubrik Security Cloud gives your organization the power to safeguard your SaaS, Cloud, and Enterprise data with secure backups, and the confidence to recover your data rapidly. Check out the rest of our videos to get insights from security experts, watch Rubrik demos, listen to podcasts, and more!