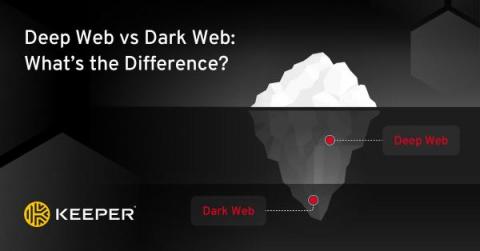
How to Help Prevent Cyberstalking
You can help prevent cyberstalking by protecting your data with a password manager, staying private on social media and following other cybersecurity best practices to keep yourself and your data safe. Keep reading to learn the best tips for preventing cyberstalking.