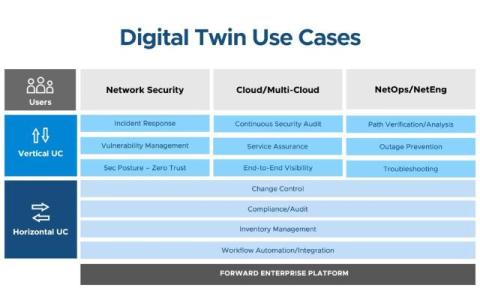
Effective Network Operations Require a Digital Twin Platform, Not a Toolbox
Tool sprawl is an expensive aspect of technical debt. IDC recently found that 43% of organizations doing business in the Americas have 500 or more software applications in their portfolios today (Application Services — Worldwide Regions, 2023, IDC #US50490416, April 2023). In the area of monitoring and observability tools alone, 50% of companies reported having between 11 and 40 tools.