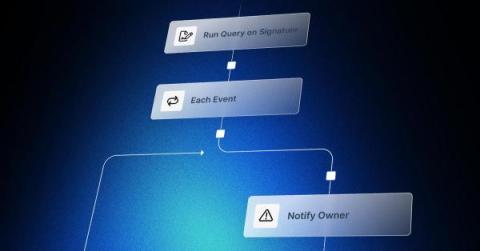
Escape SIEM LockIn Unleash a Multi-SIEM Strategy with Hyperautomation
If you are a cybersecurity professional, it’s hard to ignore the recent shift in the SIEM landscape unless you’ve been living under a rock… or more likely, under the crushing weight of terabytes worth of disconnected SIEM logs. Let’s catch everyone up to speed anyway.