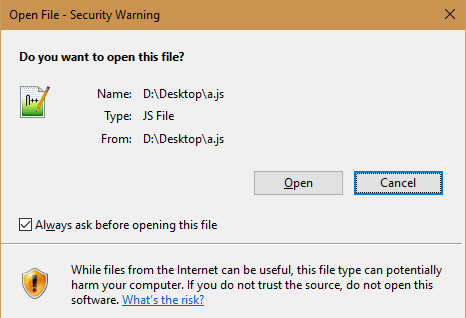
What is Enterprise Code Signing Certificate [A Detailed Guide]
Each business today requires user data to provide a better customer experience. The widespread use of data has triggered cyberattacks so much that they have become a part of software too. As per stats, there were 121 ransomware attacks in the first half of 2021. And these attacks are primarily in the form of fake software. This is where code signing and Enterprise Code Signing Certificate come into the picture.