Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Ignyte
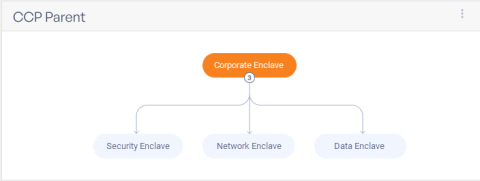
Save Time and Steps with Ignyte's Control Inheritance Automation
FIPS 199 & 200 Compliance: Comparing Security Standards
ITAR Compliance: 8 Essential Facts for Business Regulations
Navigating Authority to Operate: FISMA or FedRAMP?
Cybersecurity Standards vs Procedures vs Controls vs Policies
FAQ: What Is DFARS Compliance and How Does It Work?
The Defense Federal Acquisition Regulation Supplement, better known as DFARS, has significance for contractors working with the Department of Defense (DoD). Our intention is to offer a comprehensive perspective on DFARS in the context of cybersecurity, its various clauses, and the intricacies of maintaining compliance as these rules constantly shift and change over time.
Cracking the DISA STIGs Code: A Comprehensive Guide
We’ve talked a lot about FedRAMP, CMMC, and the typical business/contractor security controls outlined in NIST SP 800-171, but these aren’t the only elements of cybersecurity that the government wants enforced. There are also the DISA STIGS to follow. What are they, do they apply to you, and how can you follow them?
Key Takeaways from the New Proposed CMMC Rule - December, 2023
The 60-day comment period begins for the new proposed CMMC rule published in the Federal Register. The Department of Defense’s CMMC program office has broken its silence for the long awaited publishing of its new Proposed CMMC Rule on December 26th in the Federal Register.
SSP and CMMC: Why You Need a SSP for Compliance
Compliance with federal cybersecurity guidelines is three things: It’s also a very complex set of rules, guidelines, and standards that address everything from the physical security of your servers and network access to the training your employees receive. On top of that, it’s packed full of acronyms and definitions, all of which have specific meaning. SSP is one of them; it’s a critical document you need to win contracts with the government and is part of the CMMC.