Lookout Obtains FedRAMP JAB P-ATO for SASE: What It Means for You
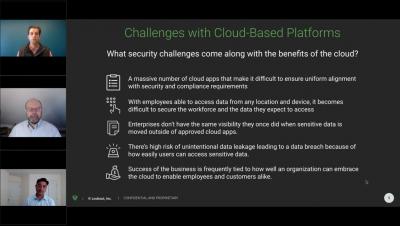
While the pandemic brought on unprecedented challenges related to full-scale telework, it has also moved cybersecurity to the top of the U.S. government’s agenda. I have been very encouraged by the various actions taken by the Biden administration, beginning with the May 2021 executive order directing federal agencies to rapidly adopt a Zero Trust architecture.