Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Kroll
Insider Threat Indicators and Detection: When Employees Turn Ransomware Accomplices
Late December 2021: A company coming off a record year for revenue growth was preparing to ramp down for a week to celebrate the December holidays. However, unbeknownst to the company, just a few days prior, one of its longest-serving employees had been recruited by a ransomware group. The employee had responded to a posting on a computer hacking forum asking for access to corporate networks in return for cash payouts.
The THIP Model: Embedding Emotional Intelligence in Third-Party Risk Management
Third-party risk management (TPRM) has grown in prominence as organizations increase their reliance on external parties, from cloud providers to credit card processors. As more enterprises invest in this critical business function, certain best practices are becoming key to a successful TPRM program.
Deep Dive Into PYSA Ransomware - The Monitor, Issue 18
PYSA is the most recent ransomware variant known distributed by the Mespinoza Ransomware as a Service (RaaS) gang, which has been infecting victims since 2019. Kroll has consistently observed PYSA in our incident response engagements since 2020 and has noted an increase in frequency of this variant since the second quarter of 2021. Our analysis shows PYSA is opportunistic and not restricted to one sector or geographical area.
Locking Your Domain Name Helps Fight Cybercrime
Ransomware and cybercrime have had a major presence in the media this past year with some very prominent attacks happening in 2021 making headlines as well as government-issued executive orders emphasizing the need for stronger cybersecurity. This has resulted in many organizations taking action to bolster their security efforts which can make it difficult for cyber criminals to successfully conduct their attacks.
How Kroll is Handling CVE-2021-44228 (Log4J / Log4Shell)
A critical vulnerability has been recently discovered in the Apache Log4j Java logging library (CVE-2021-44228), a library used in many client and server applications. The Log4j library is commonly included in Java based software including multiple Apache frameworks such as Struts2, Solr, Druid and Fink. The library provides enhanced logging functionality for Java applications and is commonly used in business system development.
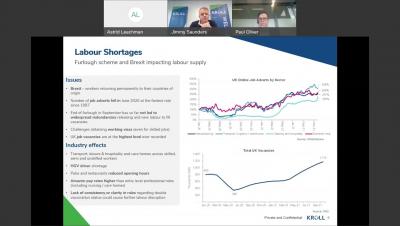
Webinar Replay | Supply Chain Disruption
IDC MarketScape: Worldwide Incident Readiness Services 2021
Named a leader in the IDC MarketScape: Worldwide Incident Readiness Services 2021 Vendor Assessment, Kroll was recognized for its portfolio of incident readiness testing and assessment capabilities fueled by frontline incident response expertise and depth of its services.
Q3 2021 Threat Landscape Ransomware in the Supply Chain
In a pattern of continued growth across the third quarter of 2021, ransomware remains the dominant threat type, more than doubling since 2021 Q1, fuelled by an exponential increase in the initial access broker marketplace. Incidents of unauthorized access and the risk of insider threats also increased, but to a far lesser extent, accounting for roughly 20% of incidents in the same period.