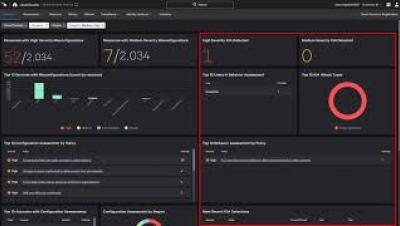
Log4j2 Vulnerability "Log4Shell" (CVE-2021-44228)
Apache has released version 2.16.0, which completely removes support for Message Lookups and disables JNDI by default. CrowdStrike has identified a malicious Java class file hosted on infrastructure associated with a nation-state adversary. The Java code is used to download known instances of adversary-specific tooling and is likely to be used in conjunction with the recently disclosed Log4Shell exploit (CVE-2021-44228).