OverWatch Casts a Wide Net for Follina: Hunting Beyond the Proof of Concept
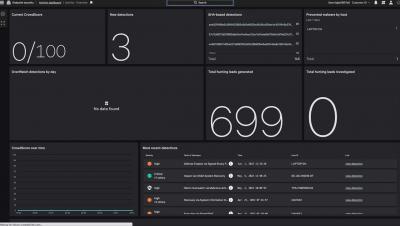
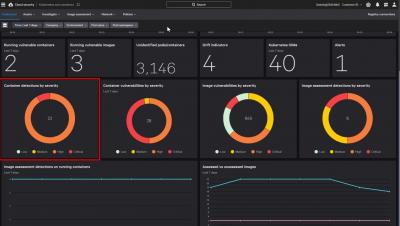
CVE-2022-30190, aka Follina, was published by @nao_sec on Twitter on May 27, 2022 — the start of Memorial Day weekend in the U.S. — highlighting once again the need for round-the-clock cybersecurity coverage. Threat hunting in particular is critical in these instances, as it provides organizations with the surge support needed to combat adversaries and thwart their objectives.