Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Sysdig
Preventing DoS attacks in Kubernetes using Falco and Calico
A Denial-of-Service (DoS) is an attack meant to shut down a machine or network, making it inaccessible to its intended users, so dos Kubernetes is a potential target. In the case of Distributed Denial-of-Service (DDoS), the attacker will look to maintain some form of anonymity so their activities cannot be traced. They can route traffic through Tor and VPN infrastructure to scan, attack, or compromise the target, while maintaining anonymous communications.
How to detect MFA spamming with Falco
Threat actors continue to evolve methods to access valid credentials using new techniques such as multi-factor authentication or MFA spamming that we must detect. On Sept. 15, the security world was worked into a frenzy across social media as details of Uber’s “cybersecurity incident” were revealed.
Extract maximum value from your Microsoft Sentinel SIEM with Sysdig Secure
Sysdig has validated its security, monitoring, and compliance capabilities with multiple Azure-related services. The latest is Microsoft Sentinel, a SIEM(Security Information and Event Management) solution on Azure that works really well with Sysdig’s cloud workload protection capabilities. Sysdig and Microsoft have a common goal of helping customers ship cloud apps faster by helping them see more, secure more, and save time in troubleshooting deployed microservices.
Building honeypots with vcluster and Falco: Episode I
Honeypots are, at a high level, mechanisms for luring attackers in order to distract them from legitimate access or to gather intelligence on their activities. We’re going to build a small example here of a honeypot using vlcuster and Falco. In this first episode, we explain how to build a simple SSH honeypot using vcluster and Falco for runtime intrusion detection.
Sysdig 2022 Threat Report: Cloud-native threats are increasing and maturing
The first annual cloud-native threat report from Sysdig explores some of the year’s most important security topics in the cloud. As the use of containers and cloud services keeps growing, threat actors are increasingly turning their attention to this new attack surface. The cloud offers unique opportunities for threat actors due to the inherent scalability and complexity of cloud resources.
How to meet 24 Google Cloud Platform (GCP) security best practices using open source
You’ve got a problem to solve and turned to Google Cloud Platform and follow GCP security best practices to build and host your solution. You create your account and are all set to brew some coffee and sit down at your workstation to architect, code, build, and deploy. Except… you aren’t. There are many knobs you must tweak and practices to put into action if you want your solution to be operative, secure, reliable, performant, and cost effective.
Falco 101 - What is Falco?
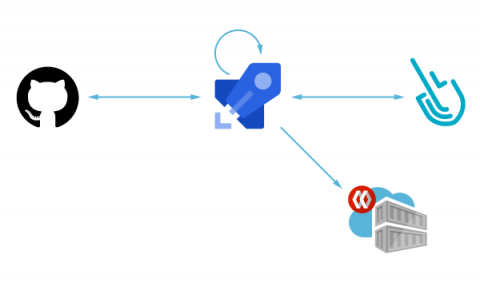
Image Scanning with GitHub Actions
Scanning a container image for vulnerabilities or bad practices on your GitHub Actions using Sysdig Secure is a straightforward process. This article demonstrates a step-by-step example of how to do it. The following proof of content showcased how to leverage the sysdig-cli-scanner with GitHub Actions. Although possible, it is not officially supported by Sysdig, so we recommend checking the documentation to adapt these steps to your environment.
Container Image Scanning for Azure Pipelines with Sysdig
Scanning a container image for vulnerabilities or bad practices in your Azure Pipelines using Sysdig Secure is a straightforward process. This article demonstrates a step by step example on how to do it. The following proof of content showcased how to leverage the sysdig-cli-scanner in Azure Pipelines. Although possible, it is not officially supported by Sysdig, so we recommend checking the documentation to adapt these steps to your environment.