Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Styra
Open Policy Agent at Scale: How Pinterest Manages Policy Distribution
New Kubernetes PCI DSS Compliance Packs, And More
As enterprises adopt cloud-first or cloud-native strategies, Kubernetes is by far the most important strategic consideration. At the same time, for the large subset of these enterprises which take payment from consumers, PCI DSS has never been more critical. More than ever, enterprises have to pay attention to data security (and their commitment to improving security posture) in order to meet compliance requirements. So what has to change to meet compliance in a Kubernetes-based environment?
Series A Financing to Continue Styra's Vision
This week, I'm pleased to announce that we closed our $14M Series A financing round. We look forward to partnering with our new investor, Accel, who led the round alongside existing investors, Unusual Ventures and A.Capital. Accel's Eric Wolford will join our board, bringing a wealth of open source experience from Heptio, SysDig and Corelight.
Minimize Kubernetes Compliance Audit Heartache
As Kubernetes matures and moves from exploration into production, we on the Styra and Open Policy Agent teams are starting to hear of a new trend. It’s part of any kind of operational lifecycle for many companies and it goes something like this: DevOps: Our Kube environment is performant, secure, and compliant by design! Auditor: K. Walk me through every line of code you typed since time began.
Investigate and Correct CVEs with the K8s API
When NIST (https://nvd.nist.go) announces a new CVE (Common Vulnerability and Exposure) that impacts Kubernetes, kube administrators and IT Security teams need to quickly understand the impact of the vulnerability and protect their Kubernetes clusters. Often, no patches are yet available, so in addition to understanding the impact, DevOps teams have to decide whether or not to create a custom fix to mitigate the risk of that CVE without bringing down the entire app or system.
How to implement guardrails for AWS EKS
Today marked the first ever AWS re:Inforce security conference, and Styra was well represented. Paavan Mistry from AWS took the stage to walk through an EKS Security session with Synamedia, wherein they talked about the great responsibility organizations have over their Kubernetes environments.
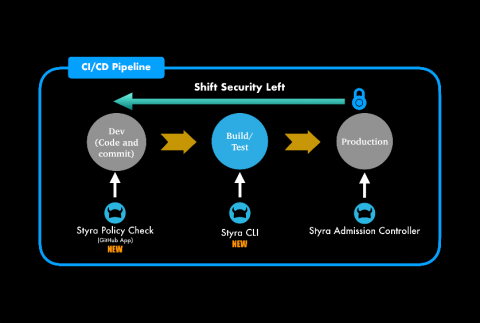
Enhancing Kubernetes Security by Shifting Security Left
In the rapidly evolving world of Kubernetes security & compliance, DevOps and DevSecOps teams are detecting security challenges and compliance issues later in the development & deployment cycles. We are excited to share new features and updates that help DevOps and DevSecOps teams detect issues and ensure compliance throughout the development cycle.
Centralized vs. Distributed Authorization: The CAP Theorem
One of the best parts of working on the Open Policy Agent at Styra is that we get to help people design authorization systems for both their platform and their custom applications. The other day we were talking someone through the design tradeoffs of authorization for their application, and the first decision they had to make was whether they wanted a centralized authorization system or a distributed authorization system. Both OPA and Styra support either, so we have no real bias.
Why RBAC is not Enough for Kubernetes Security
Kubernetes isn’t (just) fun and games anymore. It’s being rolled out for production; it’s mission-critical; and all the security and compliance rules and regulations of the old world need to somehow be retrofitted onto Kubernetes. Unfortunately, the old tools for access control like RBAC simply aren’t up to the challenge.