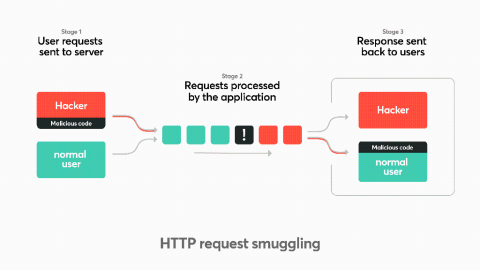
Common security misconfigurations and remediations
A misconfiguration is exactly what it sounds like; something that is wrongly configured. From a security perspective this can be either fairly harmless, or in the worst case devastating. We have written about misconfigurations before, both here and here. Misconfigurations may derive from many different reasons, such as: Hackers often exploit misconfigurations, since this can have a huge security impact.