How to Set Up Proactive Threat Intelligence
What is the best way to avoid suffering multi-million-dollar security incidents? Know your cyber enemy in advance. This means having quality threat intelligence on all the threats targeting your business, industry, or country. Let’s take a look at one of the most effective methods of collecting intel that your organization can use to better predict, detect, and respond to cyber attacks.
What is Cyber Threat Intelligence and Why Business Need It
Cyber threat intelligence (CTI) involves collecting, analyzing, and sharing information about existing and emerging cyber threats. It includes data on the tactics, techniques, and procedures used by cyber attackers, as well as known indicators of compromise, behavior, and attack. Thanks to CTI, businesses can make better security decisions to achieve:
- Timely Threat Detection: By collecting and analyzing data about cyber threats, businesses can spot potential attacks early. This helps them stop threats before they become real problems.
- Faster Incident Response: Threat intelligence provides useful information about attacks, helping companies respond quickly and effectively. Real-time monitoring allows for immediate action against ongoing threats.
- Lower Costs: Early warnings help security teams use the right tools quickly, reducing the costs associated with reacting to successful attacks.
The Importance of Collecting Threat Intelligence Proactively
Proactive threat intelligence involves actively looking for and analyzing information about potential threats before they affect your organization. This approach helps businesses stay ahead of attackers, predict their actions, and put preventive measures in place.
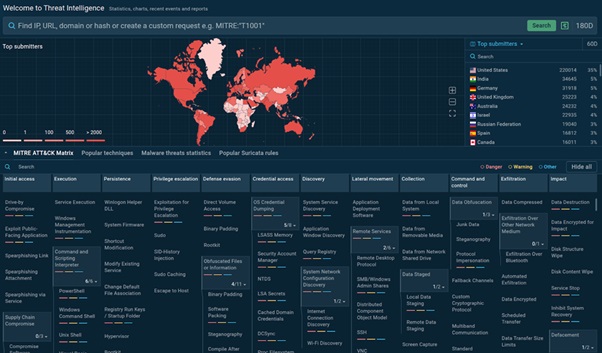
TI Lookup provides context on the latest threats with over 40 types of indicators
TI Lookup is a tool that is trusted by numerous organizations worldwide as the go-to source of proactive threat intelligence. It acts as a search engine that lets users look up over 40 different types of the latest threat data, from basic network indicators like IPs and domains to mutexes, registry keys, and Suricata IDS rules.
By submitting existing indicators or artifacts to TI Lookup, organizations quickly discover wider threat context, as well as additional details, which helps them enrich their proactive defenses.
All data points provided by TI Lookup can be linked to specific threats, like malware samples or phishing attacks, that users can analyze in full using ANY.RUN’s Interactive Sandbox.
Here are the key advantages of using TI Lookup:
- Enhanced Threat Detection: TI Lookup helps businesses spot new threats and vulnerabilities early, improving overall security.
- Faster Incident Response: By providing real-time threat data, TI Lookup helps organizations respond to incidents more quickly and effectively.
- Proactive Defense: With threat intelligence from TI Lookup, organizations can anticipate potential attacks and implement preventive measures, rather than just reacting to incidents.
|
Don't wait for the next cyber attack. Take control of your security with proactive threat intelligence. Try TI Lookup with 50 free requests to test all of its capabilities. |
How TI Lookup Helps with Proactive Threat Intelligence
One of the essential features of TI Lookup is the ability for users to sign up to receive fresh data on relevant threats. For instance, this can help organizations to stay continuously informed about the latest variants and indicators of malware that may potentially target their infrastructure and use this intel to proactively update their defenses.
Example: Tracking Geo-Targeted Phishing Threats
Suppose your organization’s German branch is getting bombarded with new phishing campaigns every week. You can set up a proactive collection of data on the phishing attacks happening in Germany by simply using this query in TI Lookup:
threatName:"phishing" AND submissionCountry:"de"
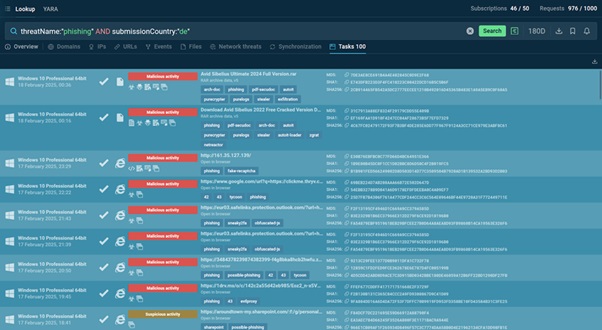
TI Lookup instantly provides the latest phishing samples uploaded by users from Germany
In response, we get a list of all the latest public samples of phishing uploaded by users in Germany to ANY.RUN’s Interactive Sandbox for analysis.
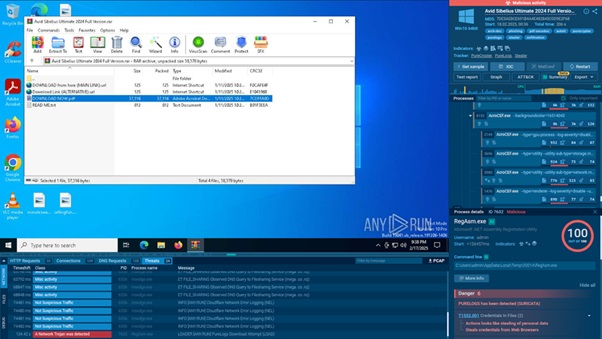
Analysis of a phishing attack featuring PureLogs malware infection
We can not only export all of the data, which includes hashes, but also dive deep into each of these phishing reports by opening them inside the sandbox.
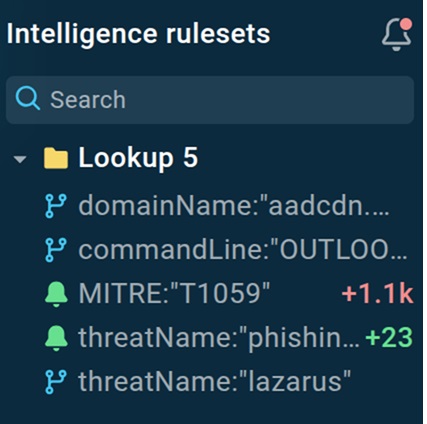
TI Lookup provides notifications on new results for the queries you subscribe to
As mentioned, we can subscribe to receive the newest results for the query we used above to never miss a single public phishing sample and get critical intel to protect the organization.
Example: Following an Advanced Persistent Threat
But what if we know that our organization is being targeted by a specific advanced persistent threat (APT), an organized group of hackers. We can better prepare for its attacks by once again collecting crucial threat intelligence on it with TI Lookup.
Let’s take the Chinese APT41 (Wicked Panda) as an example. We know that:
- They use a PowerShell backdoor to compromise systems.
- It maintains persistence by adding its payload to the Windows registry entry HKCU\Environment\UserInitMprLogonScript, allowing malicious code to run at each user login.
- The group also abuses Microsoft's legitimate forfiles.exe utility.
We can put together these details into a TI Lookup query:
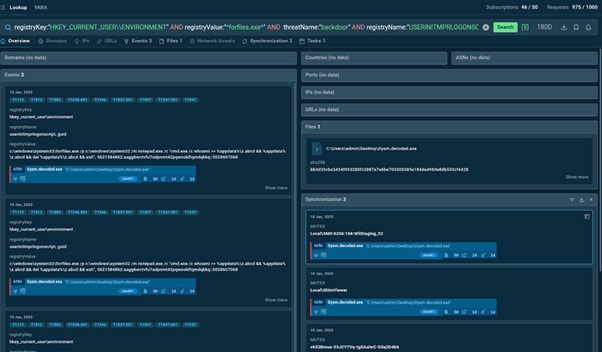
TI Lookup provides important context for the searched indicators
Thanks to this search, we uncover even more indicators, such as file hashes and mutexes, for threat detection and alerts.
Integrate TI Lookup for Proactive Threat Intelligence
Staying informed about cyber threats is essential for protecting your organization. By utilizing threat intelligence tools and proactive monitoring, you can identify and mitigate risks before they become serious issues.
Take the first step towards enhancing your cybersecurity strategy today by exploring TI Lookup with 50 free requests.

