Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
May 2023
The Bookmark Trap: How Discord Admins Fell Prey to Social Engineering
Brian Krebs wrote: "A number of Discord communities focused on cryptocurrency have been hacked this past month after their administrators were tricked into running malicious Javascript code disguised as a Web browser bookmark. "According to interviews with victims, several of the attacks began with an interview request from someone posing as a reporter for a crypto-focused news outlet online.
AI Voice-Based Scams Rise as One-Third of Victims Can't Tell if the Voice is Real or Not
As audio deepfake technology continues to go mainstream as part of the evolution in AI-based tools, new data shows there are plenty of victims and they aren’t prepared for such an attack. Imagine you get a call from your child or grandchild telling you they’re in some kind of trouble, an accident, etc. and need money. And it really does sound like them. Would you help? Scammers who are making use of AI to synthesize sound-alike voices as part of vishing scam calls are hoping you will.
Russian Ransomware Cybercriminal Behind $200 Million in Damages is Sanctioned by the U.S. Government
The U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) has identified and designated Mikhail Matveev for his role in ransomware attacks back 2021. When the U.S. sanctions a country, a business, or a group, the intent is to A) confiscate any and all property owned by the designee within the U.S. or in the possession of a U.S. person, and B) add the designee to the Specially Designated Nationals and Blocked Persons (SDN) List.
"Magic Link" Phishing Attacks Scamming Users With Fake McAfee Renewals
Threat actors are using encoded phishing links to evade security filters, according to Jeremy Fuchs at Avanan. The phishing emails purport to be notifications from McAfee informing the user that they need to renew their subscription. “This is a fairly standard McAfee subscription scam,” Fuchs says. “We see these all the time and they’ve been floating around the Internet for some time. But that’s not what makes this attack unique.
[Mastering Minds] China's Cognitive Warfare Ambitions Are Social Engineering At Scale
As the world continues to evolve, so does the nature of warfare. China's People's Liberation Army (PLA) is increasingly focused on "Cognitive Warfare," a term referring to artificial intelligence (AI)-enabled military systems and operational concepts. The PLA's exploration into this new domain of warfare could potentially change the dynamics of global conflict.
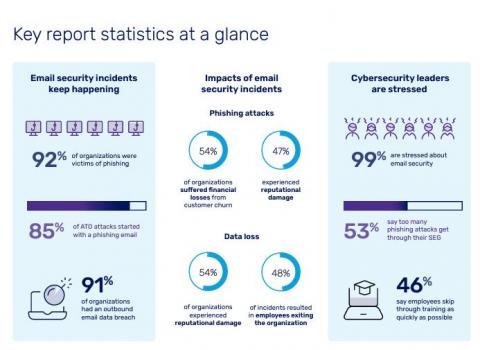
[SEG Headache] More Than Half of Cybersecurity Leaders Say That Too Many Phishing Attacks Get Through
Egress, a cybersecurity company that provides intelligent email security, recently released their Email Security Risk Report 2023. It's solid research that shows 99% of cybersecurity leaders are stressed about their email security with good reason. The numbers are scary. We mentioned their report a few weeks ago, but there are many important findings there.
Verizon Sends New Smishing Warning
Verizon has renewed its warnings to customers about the threat of smishing, a social engineering approach that relies upon texts as opposed to other communication channels like the email used in phishing. The smishing problem may be smaller than the phishing problem, or the robocall nuisance, but it represents a comparable threat that organizations should address in their risk management process.
More Than Half of all Email-Based Cyberattacks Bypass Legacy Security Filters
New data shows that changes in cybercriminals’ phishing techniques are improving their game, making it easier to make their way into a potential victim user’s inbox. I recently wrote about how 12% of all email threats were getting all the way to the inbox. But new data from cybersecurity vendor Armorblox’s 2023 Email Security Threat Report shows that the number is much higher, depending on the security solutions in place.
BatLoader Malware is Now Distributed in Drive-By Attacks
Malign persuasion can take many forms. We tend to hear the most about phishing (malicious emails) or smishing (malicious texts). Other threats are also worth some attention, like the risk of drive-by attacks. One current drive-by campaign is being run by the operators of BatLoader, a malware strain that establishes initial entry and persistence, and then can be used to distribute a range of other malicious code that loots affected systems and networks of valuable data, including funds.
Financial Fraud Phishing Attacks Increase 72% In One Year; Financial Industry Takes the Brunt
With attackers knowing financial fraud-based phishing attacks are best suited for the one industry where the money is, this massive spike in attacks should both surprise you and not surprise you at all. When you want tires, where do you go? Right – to the tire store. Shoes? Yup – shoe store. The most money you can scam from a single attack?
[Microsoft Warning] A 38% Spike In Business Email Compromise with new Cybercrime-as-a-Service
Microsoft has observed a thirty-eight percent increase in cybercrime-as-a-service (CaaS) offerings for launching business email compromise (BEC) attacks between 2019 and 2022. “Cybercriminal activity around business email compromise is accelerating,” the company said in a report. “Microsoft observes a significant trend in attackers’ use of platforms like BulletProftLink, a popular service for creating industrial-scale malicious email campaigns.
AI-generated Disinformation Dipped The Markets Yesterday
The Insider reported that an apparently AI-generated photo faking an explosion near the Pentagon in D.C. went viral. The Arlington Police Department confirmed that the image and accompanying reports were fake. But when the news was shared by a reputable Twitter account on Monday, the market briefly dipped. The photo was spread by dozens of accounts on social media, including RT, a Russian state-media Twitter account with more than 3 million followers — but the post has since been deleted.
[Hands-On Defense] Unpatched Software Causes 33% of Successful Attacks
As you all know, KnowBe4 frequently promotes security awareness training and we also mention that unpatched software is a distant number two issue after social engineering. We generally say that unpatched software is involved in 20%-40% of successful exploits. It's been hard though to get good figures on that for years and even CISA has not published hard numbers, even though they appear to focus on it.
Cyber Insurance: Is Paying a Ransom Counter-Productive?
Food for thought as discussed on May 18, 2023, an article posted in The Australian Insurance Council: Banning paying a ransom to cyber hackers is counter-productive where Andrew Hall, the Chief Executive of the Insurance Council of Australia (ICA), stated that “attempts to ban businesses from paying ransoms for cyber attacks risks eroding trust and relationships with government.”
New Top-Level Domains as Potential Phishing Risk
Google has recently introduced a set of new top-level domains: .dad, .esq, .prof, .phd, .nexus, .foo, .zip and.mov. They’re now available for purchase, and it’s the last two that are attracting attention due to the risk of abuse in phishing attacks. WIRED describes why.zip and.mov have raised concerns. “The two stand out because they are also common file extension names. The former, .zip, is ubiquitous for data compression, while.mov is a video format developed by Apple.
[New & Improved] QR Code Phishing with Snail Mail Postcards
One of KnowBe4's long-term employees just send me a picture this morning of a postcard that sure looks like it's phishing, the good old-fashioned way: snail mail! Here is the picture and you tell me what all the red flags are! The domain does not work of course. The email seems to have disappeared into the bitbucket. For many obvious reasons i have not tried the QR code since I do not have a bulletproof sandbox installed on my smartphone where I can detonate malware. :-D.
Large-Scale "Catphishing" that Targets Victims Looking for Love
For all the recent focus on artificial intelligence and its potential for deepfake impostures, the boiler room is still very much active in the criminal underworld. WIRED describes the ways in which people in many parts of the world (Ireland, France, Nigeria, and Mexico) have been recruited to work as freelancers for a company that seeks to profit from lonely people looking for love. This is how a typical operation runs.
Phishing Tops the List Globally as Both Initial Attack Vector and as part of Cyberattacks
A new report covering 13 global markets highlights phishing prevalence and its role in cyber attacks when compared to other types of attacks. It’s difficult for me not to stand on my “phishing is a problem” soapbox when there exists stories and reports demonstrating that phishing continues to dominate as a security problem that isn’t being properly addressed.
New "Greatness" Phishing-as-a-Service Tool Aids in Attacks Against Microsoft 365 Customers
This new phishing toolkit is rising in popularity for its effective realism in impersonating not just Microsoft 365, but the victim organization as well. Security researchers at Cisco Talos have identified a new Microsoft 365 toolkit that actually creates a realistic login experience for the victim user, making it more dangerous to organizations.
KnowBe4 Celebrates Success of 60,000-Customer Milestone
We are thrilled to announce we have reached a milestone of 60,000 customer organizations globally, consisting of tens of millions of end users. KnowBe4 is a customer-driven organization. I truly believe that without excellent customer service, we do not exist, which is why I regularly emphasize the importance of fantastic customer service in our daily, organization-wide meetings.
The Number of Phishing Attacks Continues to Grow at a Rate of 150% Per Year
The latest Phishing Activity Trends Report from the Anti-Phishing Working Group (APWG) shows an unrelenting upward trend in the number of phishing attacks per quarter. Despite the alarm that the growth in the number of phishing attacks should generate, this report sheds some light on what seems to be working for cybercriminals if you dig a little deeper. According to the report.
Ransomware Gangs are "Big Game Hunting" as Victim Org Sizes and Ransom Payments Continue to Rise
Midsize and enterprise organizations take notice: the average and median amount of a ransom payment and the median size of the victim organization are on the rise. If you’re at all concerned about ransomware (and you should be), the latest details from ransomware response vendor Coveware’s latest Quarterly Ransomware Report should have your attention.
78% of Ransomware Victim Organizations Encounter Additional Threats-Turned-Extortions
New data sheds light on how likely your organization will succumb to a ransomware attack, whether you can recover your data, and what’s inhibiting a proper security posture. You have a solid grasp on what your organization’s cybersecurity stance does and does not include. But is it enough to stop today’s ransomware attacks?
FTC Warns of MetaMask and PayPal Phishing Campaigns
The US Federal Trade Commission has issued an alert warning of phishing campaigns that are impersonating PayPal and the MetaMask cryptowallet. “If you got an email that seems to be from MetaMask or PayPal, stop,” the FTC says. “They’re phishing scams. The MetaMask fake says your cryptocurrency wallet is blocked. And, if you don’t act fast, click a link, and update your wallet, they say your crypto will be lost.
The State of Organizational Cyber Defenses Impacts Cyber Insurance Availability, Cost, and Terms
A new report highlights the direct connection between how strong your organization’s security stance is and how easy it is to obtain cyber insurance. Like any insurance policy, the insurer has figured out the indicators of risk and includes a form of assessment when considering issuing you a policy. When you want to obtain car insurance, they ask about your driving record, where you live, and even what your credit score is – all to determine how much of a risk you are.
The Face Off: AI Deepfakes and the Threat to the 2024 Election
The Associated Press warned this week that AI experts have raised concerns about the potential impact of deepfake technology on the upcoming 2024 election. Deepfakes are highly convincing digital disinformation, easily taken for the real thing and forwarded to friends and family as misinformation. Researchers fear that these advanced AI-generated videos could be used to spread false information, sway public opinion, and disrupt democratic processes.
U.K. Advance Fee Scams Increase by Over 600% in Less Than Two Years
New data from the U.K.’s Office of National Statistics shows that this often overlooked scam has grown significantly in interest – likely because it pays off. If you’re not familiar with this kind of scam, it’s pretty simple: the scammer presents the victim with an opportunity for a grant, a prize – something of value – but requires a small payment up front (often called a processing fee, etc.).
Cyber Insurance Demand Grows as Cybercrime is Expected to Rise to $24 Trillion by 2027
As cyber attacks continue to grow in sophistication, frequency, cyber insurers are expecting their market to double in the next two years. I’ve spent a lot of time here on this blog educating you on attack specifics, industry trends, and the impacts felt by attacks. I’ve also talked quite a bit about cyber insurance and the trends therein. But seldom have we been able to combine the two and present the state of cyber attacks from an insurer’s perspective.
Spain's National Police Take Down a Phishing Gang
A phishing (by email) and smishing (by SMS text) operation in Madrid, Seville and Guadalajara has been taken down by the National Police of Spain.
KnowBe4 Earns 2023 Top Rated Award from TrustRadius
We are proud to announce that TrustRadius has recognized KnowBe4 with a 2023 Top Rated Award. With a trScore of 9.0 out of 10 and over 800 verified reviews and ratings, KnowBe4 is recognized by the TrustRadius community as a valuable player in the Security Awareness Training category. Reviewers on TrustRadius gave high marks for KnowBe4’s overall ease of use, the variety of training and phishing content available, and great customer support.
Business Email Compromise and "Confidential" Mergers and Acquisitions
A newly identified criminal organization has been observed running a large number of business email compromise (BEC) scams. Since February 2021, Abnormal Security reports the gang has been responsible for some 350 BEC campaigns against a range of companies. No particular sector is favored, but the scammers favor larger organizations, with more than 100 of the targets being multinational corporations with offices in several countries.
Number of Ransomware Victim Organizations Nearly Doubles in March
New data shows a resurgence in successful ransomware attacks with organizations in specific industries, countries and revenue bands being the target. While every organization should always operate under the premise that they may be a ransomware target on any given day, it’s always good to see industry trends to paint a picture of where cybercriminals are currently focusing their efforts.
More InterPlanetary File System Services Use Also Means Phishing Abuse by Cybercriminals
The InterPlanetary File System (IPFS), a distributed file-sharing system that represents an alternative to the more familiar location-based hypermedia server protocols (like HTTPS), is seeing more use in file-storage, web-hosting, and cloud services. As might be expected, more use is accompanied by more abuse via phishing attacks.
Dallas Police Department is the Latest Victim of a Ransomware Attack
Unfortunately ransomware attacks have taken another victim. The City of Dallas recently confirmed that their police department suffered a ransomware attack. This attack shutdown essential services along with some 911 dispatch systems. This was announced in a statement by the city in a press release. "Wednesday morning, the City’s security monitoring tools notified our Security Operations Center (SOC) that a likely ransomware attack had been launched within our environment.
Blocking Social Engineering by Foreign Bad Actors: The Role of the New Foreign Malign Influence Center
The U.S. government created a new office to block disinformation. The new Foreign Malign Influence Center (FMIC) oversees efforts that span U.S. military, law enforcement, intelligence, and diplomatic agencies. The FMIC was established on September 23 of last year after Congress approved funding, and is situated within the Office of the Director of National Intelligence. The FMIC has the unique authority to marshal support from all elements of the U.S.
Comprehensive Anti-Phishing Mitigations: A Quick Overview
The evidence is clear – there is nothing most people and organizations can do to vastly lower cybersecurity risk than to mitigate social engineering attacks. Social engineering is involved in 70%-90% of all successful attacks. No other root cause of initial breach comes close (unpatched software is involved in 20% to 40% of attacks and everything else is in the single digits). Every person and organization should create their best possible defense-in-depth plan to fight social engineering.
[Eye Opener] HTML Phishing Attacks Surge by 100% in 12 Months
The Cyberwire reported: "Barracuda released a study this morning indicating that HTML attacks have doubled since last year. The researchers note that not only is the total number of attacks increasing, but the number of unique attacks seems to be increasing as well.
Malware Downloads Facilitated by Social Engineering
The most common route for malware infections remains social engineering in its various forms: phishing, vishing, etc. Such approaches take advantage of users’ deliberately cultivated willingness to trust communications they receive and to follow the instructions and links such malicious communications carry.
Walmart Jumps to Top of the List of the Worlds Most Impersonated Brands Used in Phishing Attacks
Walmart’s rise to become the brand most likely to be impersonated in Q1 of this year is a real problem. If you’ve been paying attention to brand impersonation in phishing attacks, you know the premise is to use a brand that a large number of potential victims do business with as a means of both establishing credibility. For many quarters, we continually saw Microsoft and/or Microsoft 365 as the brand of choice due to its wide use.
Ransomware Attacks Surge 91% in a Single Month to Reach an All-Time High
March saw a huge jump in ransomware compared to January and February, signifying that organizations should expect to see a lot more of these attacks this year. With security solutions getting good at spotting and stopping malware on endpoints and servers, you’d think that ransomware attacks would be dwindling. But, according to the NCC Group’s Cyber Threat Report for March 2023, it feels a lot more like 2023 is going to be a repeat of 2022, but at significantly higher attack levels.
Response-Based Business Email Compromise Contributes to 97% of Attacks
The malwareless and seemingly benign nature of business email compromise emails, mixed with impersonation techniques, are difficult to spot as being malicious, making them even more dangerous. I’ve covered both the threat of business email compromise and response-based email attacks before. How can I not? They are prominent techniques used by phishing scammers everywhere. But it’s the reported combination of the two by Phish Labs that has me concerned.
WSJ: "Merck's Insurers On the Hook in $1.4 Billion NotPetya Attack, Court Says"
I get the WSJ Cybersecurity newsletter, which by the way is warmly recommended. Kim Nash today reported a shocker which will make everyone's insurance premiums go even further up: "Six years after the worldwide NotPetya cyberattack, a court ruled insurers for Merck & Co. must help cover $1.4 billion in losses. New Jersey appellate division judges rejected the insurers' argument that the 2017 attack, which U.S.
Phishing as an Espionage Tactic for Cybercriminals
Phishing is a familiar criminal tactic. It’s also used by intelligence services for cyber espionage campaigns. On Friday, April 28th, 2023, CERT-UA, Ukraine’s Computer Emergency Response Team, reported that Russian operators are sending phishing emails that misrepresent themselves as sending instructions on installing a Windows security update.
The Two Best Things You Can Do To Protect Yourself and Organization
Since the beginning, two types of computer attacks (known as initial root cause exploits) have composed the vast majority of successful attacks: social engineering and exploiting unpatched vulnerabilities. These two root causes account for somewhere between 50% to 90% of all successful attacks.
[Watch Your Back] New Fake Chrome Update Error Attack Targets Your Users
Compromised websites (legitimate sites that have been successfully compromised to support social engineering) are serving visitors fake Google Chrome update error messages. “Google Chrome users who use the browser regularly should be wary of a new attack campaign that distributes malware by posing as a Google Chrome update error message,” Trend Micro warns. “The attack campaign has been operational since February 2023 and has a large impact area.”
Automate Reporting for Security Awareness Training Events and Suspicious Email Remediation Management with Cortex XSOAR and KnowBe4
Security teams face unique challenges in today’s rapidly-changing landscape of phishing, malware, and other social engineering and cybersecurity threats. Collaboration across disparate teams and siloed tools adds additional layers of complexity to security teams’ day-to-day operations. When security teams use different systems for simulated phishing, security awareness training, incident response and remediation, it is difficult to track and optimize the full lifecycle of an incident.
Phishing Attack Frequency Rises Nearly 50% as Some Sectors Increase by as Much as 576%
New data provides a multi-faceted look at the changing face of phishing attacks. This data includes who’s being targeted, the tactics being used, and why phishing attacks continue to work. If 2022 is any indication of what the remainder of this year will hold for organizations fending off cyber attacks, cybersecurity efforts are going to need a whole lot more emphasis.