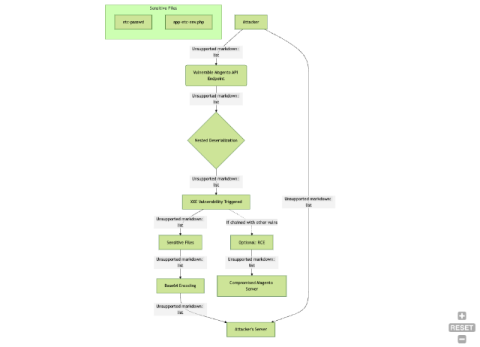
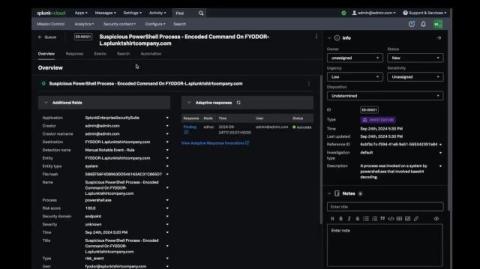
What is Privilege Escalation? An Introduction
In the realm of cybersecurity, understanding how unauthorized access can compromise sensitive systems is critical—this is where the concept of privilege escalation comes into play. In this article, we will look at what privilege escalation is, how it exploits vulnerabilities and best practices for protecting your organization against privilege escalation.