Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
June 2023
KeePass CVE-2023-32784: Detection of Processes Memory Dump
During May, a new vulnerability CVE-2023-32784 was discovered that affected KeePass. KeePass is a popular open source password manager which runs on Windows, Mac, or Linux. The vulnerability allows the extraction of the master key in cleartext from the memory of the process that was running. The master key will allow an attacker to access all the stored credentials. We strongly recommend updating to KeePass 2.54 to fix the vulnerability.
Look both ways: Preventing suspicious behavior with end-to-end detections
In the rapidly evolving digital landscape, malicious actors constantly adapt their strategies to infiltrate our systems. Traditional endpoint detection mechanisms are no longer sufficient to protect our applications and workloads against advanced threats. To effectively address this concern, it has become imperative to embrace a broader approach to threat detection. This entails a paradigm shift towards incorporating both agent-based and agentless detection methods.
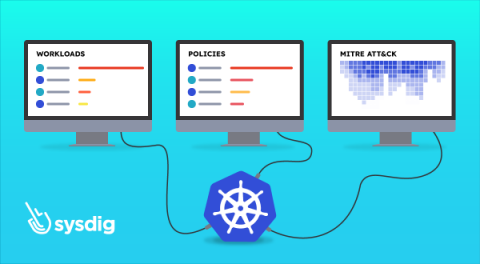
Respond Instantly to Kubernetes Threats with Sysdig Live
Discover how Sysdig Secure’s new “Kubernetes Live” informs of your Kubernetes security posture at a glance. Investigating a security incident may be a tennis match. Sometimes, you find yourself jumping from one window to another: one place for runtime events, another one for vulnerabilities, another one for logs. Gathering and correlating all the information available can be a time consuming task, but it’s the only way of having a clear view of what is going on.
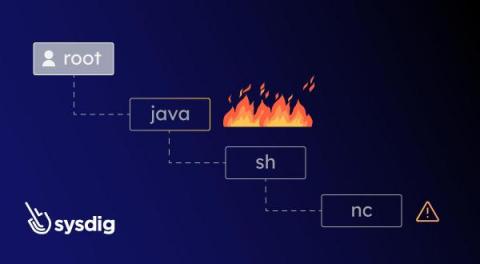
Sysdig Enriched Process Trees, an Innovative Approach to Threat Detection
Discover how Sysdig Secure’s new Process Tree feature improves threat investigation. Imagine you’re investigating a security related detection, the investigation was triggered by the execution of stat/etc/shadow in one of your containers. Is this a sign of a legitimate activity, such as a developer debugging an app, or a sign that your container has been compromised? It depends on the context.
Stop Cloud Breaches in Real Time and Accelerate Investigation and Response with Sysdig CDR
Is your organization grappling with the relentless pace of ever-changing threats in the cloud? Are you spending hours investigating security events without identifying the root cause of the problem?