Snyk and Rapid7 strengthen partnership to provide a holistic risk assessment solution for container applications
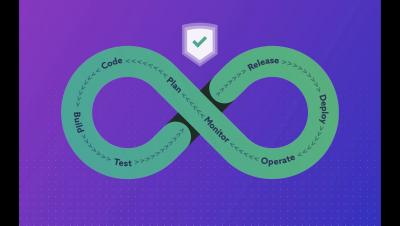
Modern organizations are working hard to differentiate their products and services by creating innovative solutions that their customers can leverage at home and on-the-go, forcing them to consider new, more agile approaches to application development that empower their development teams to accelerate time-to-market, and launch new solutions as quickly as possible.