5 Important SIEM Reports
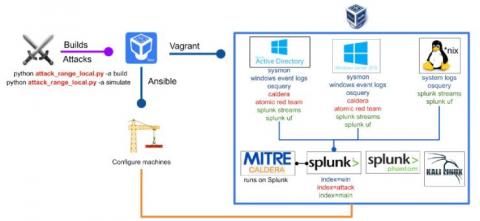
Security Information and Event Management (SIEM) helps organizations in collecting, correlating, and analyzing log data from a wide range of systems connected to their IT infrastructure. Based on the results, a SIEM solution assists an organization in detecting threats and suspicious activity on their IT infrastructure. If you are already using a SIEM platform such as Logsign, you would know the importance of SIEM reports.