Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Automotive
How Secure is Automotive Digital Identity?
EP 48 - What's Driving the Future of Automotive Security
Cybersecurity in automotive - why automotive companies should consider a DevOps backup for Jira, GitLab, GitHub, and Bitbucket
#97 - Cybersecurity threats to electric vehicles with Mike Pedrick, CISSP at Nuspire
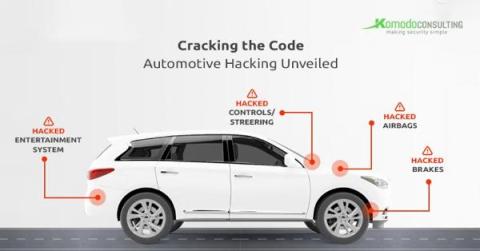
The Rise of Automotive Hacking
The automotive industry stands at the crossroads of innovation and vulnerability. As cars become increasingly connected, with advanced systems and features that rely on intricate software, the rise of automotive hacking has become a pressing concern. The convergence of traditional mechanical engineering and cutting-edge software has given rise to a new breed of threats that extend beyond physical security, delving into the digital realm of vehicle control systems.
How Self-Learning AI Has Helped CARIAD Build An Automotive Software Powerhouse
Automotive Industry stalling ahead of 2024's new vehicle safety regulations
With the United Nations Economic Commission for Europe World Forum for Harmonisation of Vehicle Regulations (UNECE WP.29) framework coming into effect in July 2024, leaders across the Automotive sector are apparently ‘swamped’ by the volume of compliance and security risks that need to be addressed to protect drivers in all types of connected or autonomous vehicles.
Connected Cars, Exposed Systems: The Cybersecurity Challenges of IVI Platforms
Why Automotive Companies Must Prioritize Secrets Detection
Explore the critical role of secrets security in the era of software-driven vehicles. From code leaks to supply chain vulnerabilities, read how safeguarding automotive software is paramount for consumer safety.