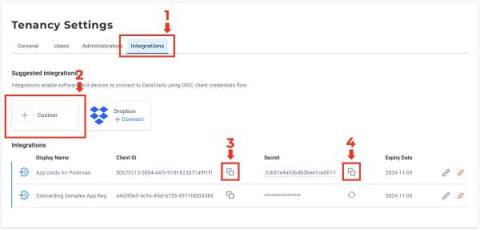
RKVST is now DataTrails!
We’ve listened, we’ve learned, and the market has definitely spoken! Our old name just wasn’t working: it was hard to pronounce, hard to spell, and hard to understand what we do. Even if the ‘archivist’ leap was made it didn’t carry our special mission with it.