Customize your Access Policies with DataTrails
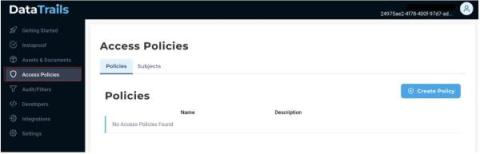
Signing up with DataTrails comes with the ability to share your audit trails with your business partners, other applications, and your internal team. Access policies control users, apps & organizations’ read & write privileges to provenance data in DataTrails. If you’re using an integration, access policies offer a way to fine-tune these integrations, giving specific permissions to add to and read your records.