Securing Database Access: DPA Zero Standing Privilege Approach with Native pgAdmin Utility
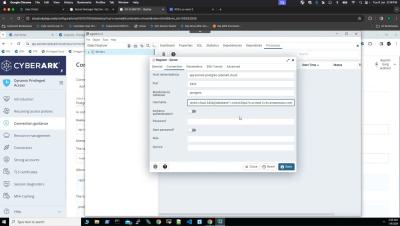
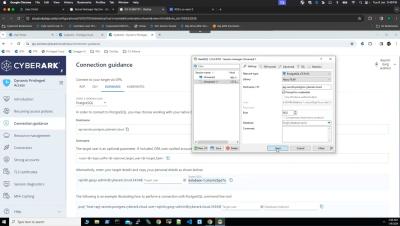
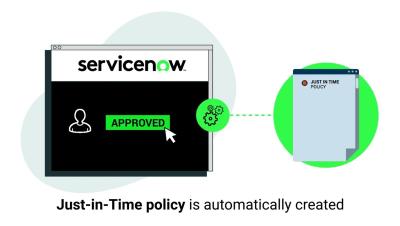
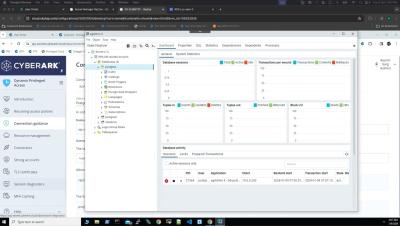
In this video, we'll guide you through the process of utilising CyberArk DPA's capabilities to seamlessly connect to a Postgres database using the PGadmin client, leveraging the secure foundation of JIT access approach for enhanced security and efficiency.