Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Access Management
How Does a PAM Solution Help Organizations Meet CIP Cyber Security Standards?
The North American Electric Reliability Corporation’s Critical Infrastructure Protection (NERC CIP) standards are a comprehensive set of requirements that ensure the security and reliability of the North American power grid. These standards address both the physical security and cybersecurity of the bulk electric system, mandating measures to protect critical assets from potential threats.
Minimizing Your Enterprise Attack Surface
Keeper Security Report: Organizations Seek Cloud Advantages in PAM Solutions
Keeper Security has released the third part of its series on Privileged Access Management (PAM) research, the Keeper Security Insight Report: Cloud-Based Privileged Access Management, to determine what IT leaders are seeking in a PAM solution and the benefits of moving away from traditional, on-premises platforms.
What is IAM (Identity and Access Management)?
Improving security and efficiency with IDaaS
Reduce the Noise to Secure Your Environment
OneLogin Workforce Identity Demo
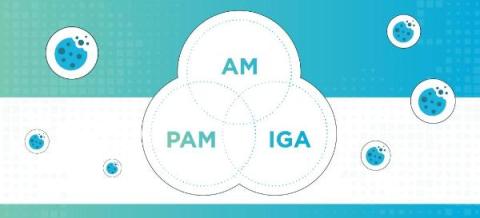
Strengthening Cyber Defenses: The Crucial Role of PAM and IGA Solutions
We recently published a blog titled Defending Your Organization Against Session Cookie Replay Attacks. This blog thoroughly examined the menace of session cookie replay attacks, shedding light on the potential risks and consequences they pose to online security. The post delved into the intricacies of session cookie replay attacks, detailing their working mechanisms and the extensive damage they can inflict and emphasizing the imperative need to comprehend and fortify against such threats.
Defending Your Organization Against Session Cookie Replay Attacks
In the current cyber threat landscape, where online security is paramount, the threat of session cookie replay attacks looms large. These attacks sidestep the conventional need for credentials and aim to hijack your online sessions, potentially compromising sensitive data and taking over user accounts. This blog post delves into the intricacies of session cookie replay attacks, shedding light on what they are, how they work, and the potential consequences they can unleash.