Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Alerting
Forward Fix: Use Case for Splunk Custom Alert to trigger Forward Networks Snapshot
Accelerate Incident Response and Incident Management with AIOps. 5 Key Benefits in Cisco Environments
Artificial Intelligence for ITOps (AIOps) can help accelerate incident response with all the incident context, impact assessment, triage data and collaboration & automation tools at one place.
Doing AIOps Right: Addressing Monitoring Gaps with Observability-in-a-Box
Are your current expensive, traditional or legacy monitoring tool implementations holding you back? It may be time to look into Observability architectures.
CloudFabrix featured in "Top 20 vendors shaping IT Performance" by Digital Enterprise Journal (DEJ)
Emerging digital IT paradigm shifts like Hybrid IT, Multi-Cloud, Microservices & Containerization, Serverless, Software Defined Datacenter etc. are creating compelling new opportunities for IT leaders. However, these same paradigm shifts have also led to a drastic increase in monitored assets, numerous operational tools, and exponential growth of operational data.
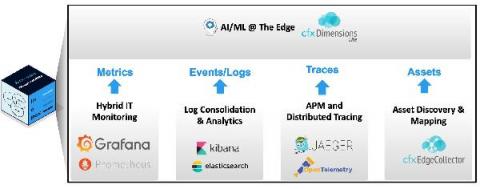
CloudFabrix announces Observability-in-a-Box with Edge AI Capabilities to simplify and accelerate AIOps deployments
CloudFabrix is enhancing its AIOps platform with native Observability and AI at the edge capabilities to bridge the gap between Observability and AIOps solutions. Enterprises are struggling with unifying multitude of expensive monitoring deployments as well as gaps in observability, specifically for modern application architectures that include usage of microservices, containers and Kubernetes.
Alert Fatigue And Automation Fatigue
Alert fatigue is a well-known phenomenon with security products – the security team gets a lot of alerts (from the SIEM, for example), it tries to triage and act upon all of them, but at some point, they are so many and so few of them are actual threats, that the security team just ignores them. And that leads to both overworked security teams and an increased risk for missing an actual threat. Why is that happening? It’s hard to tweak a system right, no matter how flexible it is.
Detecting Security Vulnerabilities with Alerts
Every day we discover new vulnerabilities in our systems, cracks in the fence the adversaries take advantage of to get into your organization and wreak havoc. Understanding what you have in your environment (e.g., types of devices, systems equipment, etc.) is very important in order to make sure the controls in place are working and more importantly, keeping up with the threat landscape.
SIEM Alerts Best Practices
Security Information and Event Management (SIEM) tools play a vital role in helping your organization in discovering threats and analyzing security incidents. Logsign’s internal team continuously makes correlation rules and alerts so that your team’s workload is minimized. In our previous posts, we discussed generating important reports and deriving maximum possible benefits from use cases. In this article, we will be discussing SIEM alerts best practices.