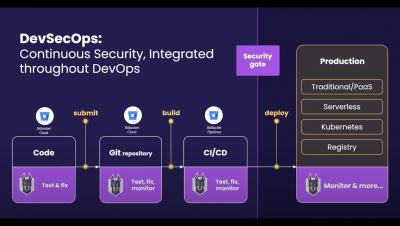
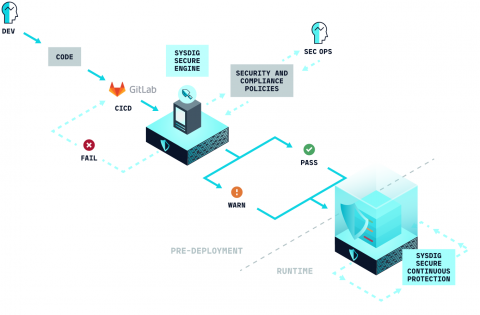
CI/CD combines the practices of continuous integration (CI) and Continuous Delivery (CD) to allow DevOps teams to deliver code updates frequently, reliably, and quickly. CI/CD emphasizes automation throughout the development lifecycle (Buid, Test, Deploy). By replacing the manual efforts of traditional development, code releases can happen more frequently, and with less bugs and security vulnerabilities. At CrowdStrike, we focus on integrating security into the CI/CD pipeline. As part of the functionality of CrowdStrike’s Falcon Cloud Workload Protection (CWP), customers have the ability to create verified image policies to ensure that only approved images are allowed to progress through the CI/CD pipeline and run in their hosts or Kubernetes clusters.