Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Machine Learning
Trustwave MailMarshal PageML Scanner Detects 30% More Phishing Attempts
Trustwave’s MailMarshal received a major update this month with the addition of PageML to the Blended Threat Module. The BTM enables the email security solution to conduct in-depth, real-time scans when a URL in an email is clicked to determine if the URL is malicious. PageML boosts the BTM’s ability to detect malicious URLs by one-third by applying machine learning techniques to page content in real time. The new scanning feature is named PageML, short for Page Machine Learning.
CrowdStrike's Free TensorFlow-to-Rust Conversion Tool Enables Data Scientists to Run Machine Learning Models as Pure Safe Code
Deep learning is a core part of CrowdStrike’s arsenal of machine learning (ML) techniques, and we are constantly innovating in this area to boost the performance of our ML models. However, ML can consume large amounts of computing resources. To minimize the computing load and its associated costs, we strive to optimize performance and resource utilization for our models as well as address any safety issues related to the use of third-party tools.
What is Meant by Applied Quantum Computing?
Using Artificial Intelligence and Machine Learning to Combat Hands-on-Keyboard Cybersecurity Attacks
With news headlines like “A massive ransomware attack hit hundreds of businesses” becoming common, concern about malware has never been higher. High-profile examples of malware like DarkSide, REvil have been profiled so many times that not only cybersecurity professionals are on edge — every organization that has on-premises or in-the-cloud workloads is concerned.
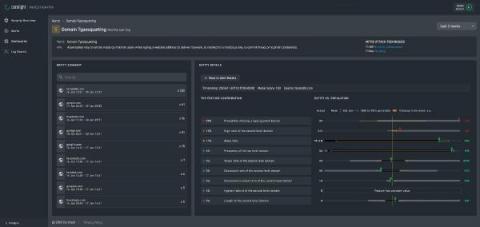
Corelight Investigator introduces new Machine Learning Models
Corelight Investigator furthers its commitment to delivering next-level analytics through the expansion of its machine learning models. Security teams are now enabled with additional supervised and deep learning models, including: We continue to provide complete transparency behind our evidence -- showing the logic behind our machine learning models and detections, allowing analysts to quickly and easily validate the alerts.
5 Machine Learning trends businesses should be aware of in 2023
One thing’s for sure: in 2023, Machine Learning will penetrate even more businesses in even more sectors, following tremendous growth last year. But when it comes to ML, what should organizations have their eyes on, to stay ahead of their competitors?
How Machine Learning as a Service improves organizational productivity and reduces costs
85% of Machine Learning (ML) projects fail. This stark reminder from Gartner – despite more tools being available to businesses than ever. The thing is ML success is not just about tools and technology; it’s about how they’re put into production by experts. Plural. Machine Learning – that improves productivity and profitability by finding valuable insights buried deep in your company databases – needs a small army to leverage it.
Machine Learning. Security Friend or Foe?
Recent advancements in machine learning, the latest on Black Proxies, and the DHS Cyber Safety Board’s plan to review Lapsus$ gang’s hacking tactics.
Machine Learning in Security: Deep Learning Based DGA Detection with a Pre-trained Model
The SMLS team enables Splunk customers to find obscure and buried threats in large amounts of data through expert analytics. This work is part of a set of machine learning detections built by a specialized team of security-focused data scientists working in concert with Splunk’s threat research teams to help Splunk customers sift through vast amounts of data to identify and alert users of suspicious content.