MSSPs: Streamline your customers' operations with Tines
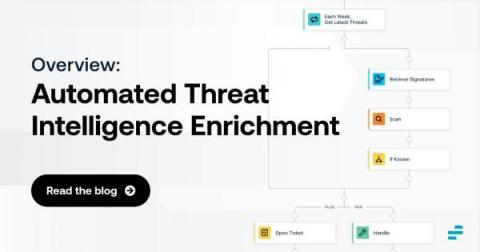
Today, MSSPs are trying to scale their businesses quickly, onboard customers with high-quality tool sets that evolve with the company, and maintain or increase margins. This means reducing costs, improving onboarding time, and building the next generation of MSSP (Managed Security Service Provider) or MDR (Managed Detection and Response) company. Threats in their own and customer environments continue to grow for MSSPs, as does the technology stack to support them.