Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
What is SSE? #shorts
New Report from the WatchGuard Threat Lab Shows Surge in Endpoint Ransomware, Decline in Network-Detected Malware
Vanta Deepens International Momentum with Launch of EU Data Centre
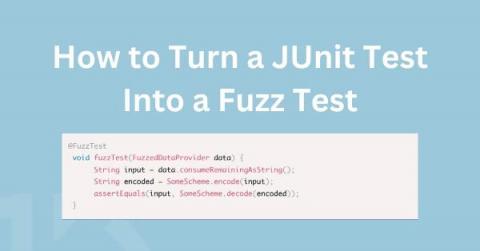
Level Up Your Unit Tests: How to Turn a JUnit Test into a Fuzz Test
16 Ways Cloud WAFs are Better than On-Premise WAFs
What You Need to Know About the 3CX Supply Chain Attack
Defend against insider threats with LimaCharlie
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) defines insider threat as “the potential for an insider to use their authorized access or understanding of an organization to harm that organization.” The nature of insider threats is fairly wide-ranging. Most of us in the security field will naturally think of insider threats in cybersecurity terms, but CISA’s definition includes things like espionage, terrorism, and workplace violence.
Employee Rewards Automation: A Case Study of Exposed PII in Power Automate
In recent years, companies have been looking for ways to streamline their HR processes and make them more efficient. In recent years it has become practically feasible for business users such as HR professionals to create their own solutions, due to the wave of citizen development which is exploding worldwide. Huge market players perceive this as a growth area and are heavily investing in providing solutions and platforms to enable business users to build what they need, when they need it.
Enhanced security in JFrog Artifactory using Bytesafe
In the ever-evolving world of software development, secure and efficient package management is crucial to maintaining code integrity and fostering collaboration. While JFrog Artifactory offers a powerful solution for repository management, integrating Bytesafe as an upstream source can further enhance security and collaboration capabilities.