PCI DSS 4.0: How to Delight the Auditors
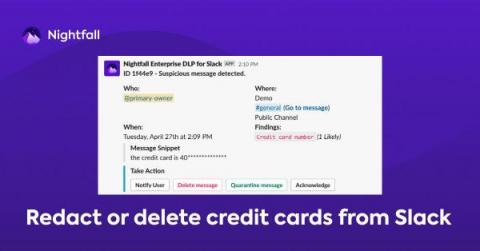
While we all know the actual point of PCI is vastly more far-reaching, we can’t deny that the juggernaut of PCI DSS 4.0 compliance is getting past the auditors. However, there is a right way to do it that doesn’t just check the box – it creates the underlying business operations that enable you to pass an audit any day, at any time, with just the processes you have in hand. Here’s how.