Relaunching BDRCloud: Cost-Effective Cloud-Hosted Backup & Recovery Solution - BETA Available Now!
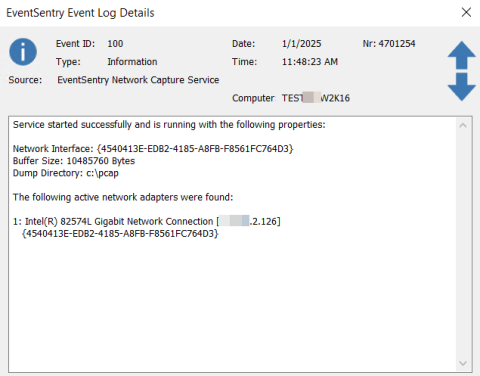
We are excited to announce the relaunch of BDRCloud, now more cost-effective than ever! BDRCloud is a comprehensive backup and recovery solution designed for MSPs and businesses, simplifying data protection with cloud-based management.