Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Positive Risk vs. Negative Risk in Enterprise Risk Management
Businesses face risk all the time – and that’s OK. Even though the word “risk” typically has negative connotations, the term can actually represent many situations, not all of them unfavorable. ISO 31000 states that risk is the “effect of uncertainty on objectives.” That actually means risk can come in two types: positive and negative.
Data Loss Prevention (DLP) Systems: Types, Key Features, Pros and Cons
API Security Testing: Importance, Risks and Checklist
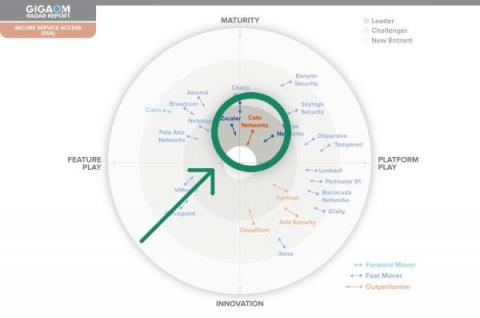
Cato SASE Cloud: A Two-Time Leader and Outperformer in GigaOm's Radar Report for Secure Service Access
In the ever-evolving world of cybersecurity, enterprises are constantly seeking the most effective solutions to secure their networks and data. GigaOm’s Radar Report for Secure Service Access, GigaOm’s term for SASE, provides a comprehensive look at the industry, and for the second consecutive year, names Cato Networks a “Leader” and “Outperformer.” The recognition points to Cato’s continuous commitment to innovation and improvement.
What is a Whaling Attack and How to Prevent It
Five worthy reads: Strengthening cybersecurity-exploring vital legal provisions
Five worthy reads is a regular column on five noteworthy items we’ve discovered while researching trending and timeless topics. This week we are exploring vital legal provisions to strengthen cybersecurity. The digital environment has developed into a fertile ground for cybercrime in today’s connected society. Governments all across the world have realized the need for extensive legislative protections for people, organizations, and national security due to the increase in cyberattacks.
Cryptographically Relevant Quantum Computers (CRQCs) & The Quantum Threat in 2023
Cryptography and network security: The quick and short guide
There is an old joke among cybersecurity professionals that the only way to truly secure your data is to keep it on a machine without connection to power or the internet… oh, and put it in a sealed cave. And even then, it is not 100% secure. In today’s world, it’s a pretty safe assumption that none of our data is truly secure.
Teleport Achieves ISO 27001, HIPAA, and SOC 2 Compliance Milestones
We're thrilled to announce that Teleport has recently achieved critical compliance milestones, marking another significant step forward in our commitment to providing highly secure and reliable cloud-based services. We are pleased to inform you that Teleport has successfully achieved ISO 27001 certification, is now HIPAA compliant, and has also expanded our SOC 2 report coverage with the addition of Confidentiality and Availability trust service criteria.