Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Escape Python's Stranglehold With AWS CLI
The Botnet siege: How your toaster could topple a corporation
In addition to the overt signs of cyber threats we've become conditioned to recognize, like ransomware emails and strange login requests, malicious actors are now utilizing another way to achieve their nefarious purposes — by using your everyday devices. These hidden dangers are known as botnets. Unbeknownst to most, our everyday devices, from toasters to smart fridges, can unwittingly be enlisted as footsoldiers in a digital army with the potential to bring down even corporate giants.
There was a cyberattack every 39 seconds in 2023
Cyberattacks continue to be a cause for concern for businesses. Although great strides have been made to combat this issue, the ability of threat actors to adapt, combined with other factors such as the rise in remote working or the increase in the number of devices with Internet access, means that cybercrime persists. According to a study by Cybersecurity Ventures, a cyberattack took place every 39 seconds in 2023, which translates into over 2,200 cases per day.
Securing JavaScript: Best Practices and Common Vulnerabilities
JavaScript is the most commonly-used programing language, according to the most recent StackOverflow developer survey. While JavaScript offers great flexibility and ease of use, it also introduces security risks that can be exploited by attackers. In this blog, we will explore vulnerabilities in JavaScript, best practices to secure your code, and tools to prevent attacks.
Data Breach Defined & Ways To Prevent One in 2024
CrowdStrike Falcon Platform Delivers $6 Return for Every $1 Invested
A new IDC white paper, “The Business Value of The CrowdStrike Falcon XDR Platform,” sponsored by CrowdStrike, highlights the substantial operational benefits, cost savings and ROI that organizations achieve when consolidating their cybersecurity point products with the AI-native CrowdStrike Falcon XDR platform. Organizations switching to the CrowdStrike platform realized significant advantages.
3 Things To Know About Securing Remote Work with VPN
It's been two decades since the introduction of virtual private networks (VPNs), and they are still the go-to solution for many organizations that need to connect remote users to company resources. But while VPN technology remained relatively static — grounded on the principle that your resources are primarily located on a corporate network — remote work requirements have changed dramatically.
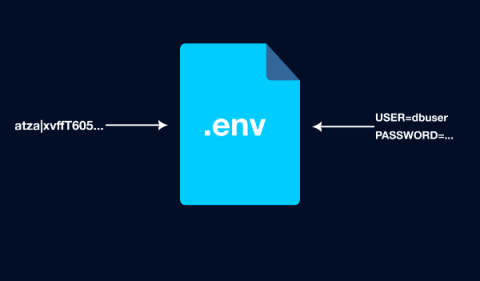
Secure Your Secrets with .env
Using environment variables to store secrets instead of writing them directly into your code is one of the quickest and easiest ways to add a layer of protection to your projects.
The CISO's Guide to a Modern GRC Program with Trust Assurance
The position of CISO is not an enviable one. Modern CISOs face enormous challenges like managing the complexity of on-prem and cloud environments, being responsible for the actions of thousands of employees without having authority over them, being perceived as a drag on growth and other resources, and trying to keep up in a compliance and technology landscape that just keeps changing. Oh and budget? Limited and scrutinized.