Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
October 2022
Noname Security Announces Partnership with Health Insurance Leader Aflac
Announcing Release 3.4
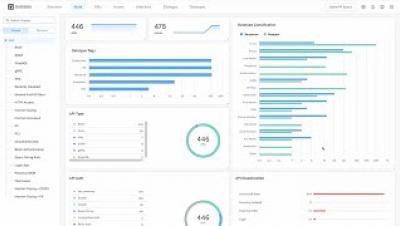
We’re excited to announce the release of 3.4, the latest set of additions and enhancements to the Noname API Security Platform. Noname’s research & development team – the largest of its kind dedicated to API security – is constantly improving the Noname Platform with new releases made available to customers every few weeks.
Continuous Security for APIs
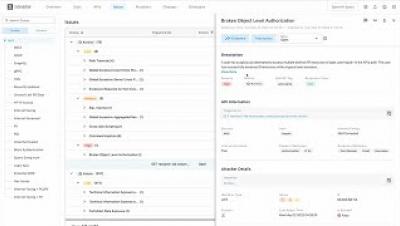
Mitigating OWASP Top 10 API Security Threats
Noname Security Bolsters C-Suite by Appointing Ran Harpaz as First Chief Operating Officer
Introducing the Noname API Security Workshop
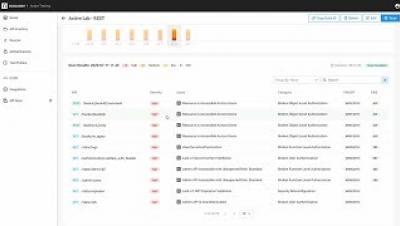
Discover All Your APIs
Block API Attacks in Real-time
Deliver Secure APIs with Active Testing
End-to-End API Security
Doing security properly for application programming interfaces (APIs) is a process that goes well beyond security. It’s also about IT operational and architectural issues that drive security outcomes. To be successful, API security must be viewed as an end-to-end process covering the full software lifecycle. It starts with development but continues through runtime and end-of-life.
Optus Data Breach - Why Vulnerable APIs are to Blame
For those that haven't heard, Optus, the second largest telecom company in Australia, exposed over 11.2 million customer records including names, physical and email addresses, birth dates and, for some, government issued id numbers such as drivers license or passport numbers. Yoikes.Optus hasn't provided many specific details so far but there's plenty to consider.